The emergence of Coronavirus (hereafter COVID-19) and its rapid spread has emerged as a pandemic situation in which the majority of the worldwide population has no choice but to stay safe at home. According to Microsoft’s Bing “COVID-19 tracker” data on 05 May 2020, the total number of “active” cases counts to 2,164,603 and fatality counts to 251,580 worldwide.2 In India (as of 05 May 2020), the total active cases of COVID-19 counted 31,967 and fatality counted to1,583.3 As a precautionary measure against COVID-19, several countries, including India have declared ‘lockdown’— an emergency protocol applied in which people are not allowed to enter or leave a building or an area freely.4 The objective of the lockdown is to contain the spread of COVID-19 in a country. In his address to the nation on 24 March 2020, Indian Prime Minister (PM) Narendra Modi declared the nationwide lockdown started from 25 March for the next 21 days, i.e. till 14 April 2020.5 Later, on 14 April 2020, PM Modi addressed the nation and announced the extension of lockdown till 03 May 2020, and subsequently from 04 May 2020, the lockdown has been extended till 17 May 2020, with specific relaxations and guidelines to follow, given the rise in cases and importance of fight against COVID-19 in India.6
PM Modi urged the citizens to stay inside their homes and cooperate with the government issued guidelines to contain the spread of COVID-19 in India. The 11 high-powered committees (formed by PM Modi) have received the request from many State governments and experts to extend the lockdown period. Some of the recommendations included the closure of schools and colleges till June 2020 with no exceptions, and the restrictions shall also apply to all religious gatherings with no relaxations.7 Acting upon the governments’ guidelines against COVID-19 pandemic and as a foremost step of employees’ safety, several organisations (excluding emergency services) around the globe have applied ‘work from home’ policy. In India, companies of all sectors have no choice but to follow the work from home practices following the government’s ‘strong advisory’. The advancements in technology and accessibility of the Internet has eased the pressure of work of the individuals by staying connected virtually and carrying out the responsibilities towards the organisation. Through the social-distancing in the work-from-home scenario, the transmission of COVID-19 may have been contained to an extent. However, during the lockdown and work-from-home situation, the usage of the Internet for work, social networking, dissemination and absorption of news/information, and other entertainment purposes have exposed the digital devices/information systems/computers to vulnerabilities and attacks in the cyberspace.
Extension in Lockdown & Rise in Cyber Crimes
According to the officials from the Ministry of Home Affairs (MHA), “there have been 86 per cent rise in cybercrimes” since March 2020.8 In the lockdown scenario, the cybercriminals may victimise people using either of several modus operandi, such as “phishing”, “malware attacks”, “child sexual abuse”, “fake news”, “identity theft”. In the first week of April 2020, Maharashtra police filed a case against an unidentified online fraudster who placed an advertisement on OLX— an online marketplace, tried to sell the ‘Statue of Unity’ for USD 4 billion, claiming that the money will be utilised to support Gujarat government in tackling COVID-19 situation.9 According to the 2019 Internet Crime Report published by the Federal Bureau of Investigation (FBI)’s Internet Crime Complaint Centre (IC3), among top 20 international Internet-victim countries, India ranked at 3 (three), after the United Kingdom (rank 1), and Canada (rank 2).
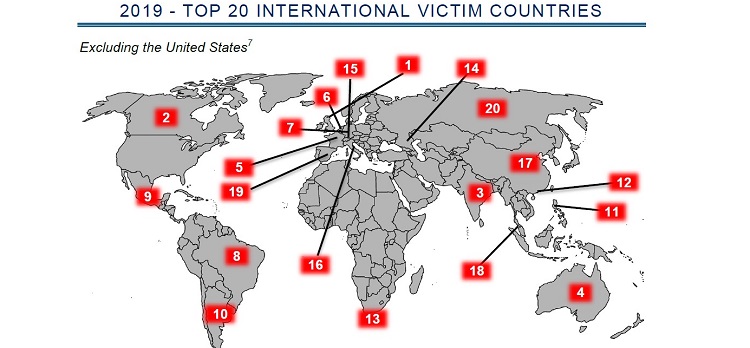
Image 1: “Top 20 International (Internet) Victim Countries” [Source: IC3.gov]
Cybercrimes respects no geographical borders and evolves at a faster pace with the facilitation of the Internet. According to Norton LifeLock 2019 Cyber Safety Insights Report, of 10 countries, almost 500 million people were cybercrime victims in comparison to almost 350 million people in 2018.10 The same report highlighted the percentage of “government”, “companies”, and “individuals” responsible for cyber safety in the same ten countries.
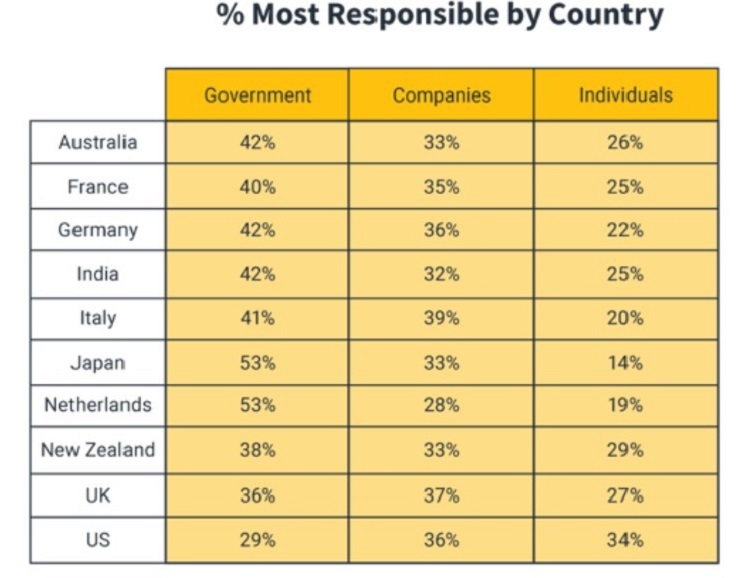
Image 2: Country-wise most responsible for personal information protection and data privacy. [Source: Norton LifeLock Cyber Safety Insights Report 2019]
As per data highlighted in the above chart, in India, the government put more measures to the protection of information and data privacy (42 per cent), followed by the companies (32 per cent), and individuals/consumers (25 per cent). The similar situation is with most of the countries, except the United States. In the United States, the consumer/individual percentage has outranked the government percentage responsible for protecting personal information online and data privacy. Cyber criminals are not only targeting the businesses but the information systems of hospitals and healthcare professionals. In a situation, a cyber criminal may apply different modus operandi in a single cyber attack. For example, initiating a phishing attack, a cyber criminal may install malware on the information systems of the hospital and placed ransomware in exchange for the medical records of the patients. Following sections shall discuss some cyber-attacks common during the lockdown situation.
Phishing Attacks
The word “Phishing” may spell differently to “Fishing” but has a similar modus operandi in the cyberspace. In the digital world, cybercriminals pose as a legitimate identity randomly or specifically target a person to obtain her/his personal/confidential information via an email-based attack. The objective of phishing may include obtaining financial data, personal information, or downloading a program, usually malware, for further access to the information system. Likewise, ‘Fishing’, unknowingly the users get swayed with the fake ‘lure’ and ‘bite’ by providing the information which cybercriminals have requested. In a report by Norton Security Solutions, Phishing requests made to second place in “Top 5 Social Media Scams”.11 Such phishing scams involve a significant amount of social engineering as a tactic, which influences the victim to get lured. As the modus operandi, the cybercriminal may create a fake e-mail with a link directed to a fake webpage. The moment an individual clicked on the link, it will land on the fake webpage that looks very similar to the original webpage. Unknowingly, the user may supply all the information requested by the cybercriminal. China, the origin of COVID-19, has not lacked behind in attacking the computer systems worldwide deploying phishing attacks. In March 2020, the ‘Chinese’ APT group— Mustang Panda delivered malicious codes through multiple spam campaigns.12 The malicious codes were used in e-mail and other communications to compromise the target’s cyber-infrastructure.
During the nationwide lockdown, there has been a manifold increase in phishing-related cases. A senior officer of the Maharashtra police cybercrime department (on condition of anonymity) has informed that since the first lockdown, phishing cases have increased by 25 per cent in following two weeks, i.e. 24-March to 05 April 2020.13 The targets are not only individuals but companies as well. Due to the ramifications of work-from-home, proprietary data of companies are being accessed from laptops or PCs (Personal Computers) using the Internet connection available at home. Such Internet connections may not be as secure as the company’s network—equipped with firewall and other network security solutions. In a phishing case, the cybercriminals may offer fake maps related to COVID-19 infected people in a particular State/city/area and require a person to download the application out of curiosity and panic. Downloading and installing such malicious applications would be a security concern as the application may have an embedded malware or malicious program to fetch the information from the device without users’ consent.
Malware & Ransomware Attacks
The unfortunate situation of COVID-19 and measures to combat its further spread has allowed cybercriminals to prey on people who are desperate to protect themselves and others by referring to the Internet for solutions. In a report by the ICANN (Internet Corporation for Assigned Names and Numbers), in March 2020, around 100,000 new website domain names were registered worldwide centric to keywords— “covid”, “corona”, and “virus”.14 According to Andre Pienaar—founder of the C5 Capital firm, the United State (US) and Europe, there are a number of cases where COVID-19 testing labs and major hospitals have been the victim of ransomware attacks.15
Apart from phishing, “Malware” and “Ransomware” there are other forms of sophisticated cyber-attacks. Equipped with old techniques such as “trojans”, the new malware programs are designed to target the computer systems and most mobile devices. As an example, Riltok, which is a money-stealing malware, targeted from Russia to the rest of the world. Discovered in March 2018, Riltok hides malicious code within the native code of its program. As a malware designed as a Trojan, Riltok gained access to the financial data and assets on the targeted smart phones/mobile devices by tricking the user into installing the disguised version of a legitimate banking application and stealing the log-in credentials. 16 In the United States alone, there has been a spike in the numbers of ransomware-led attacks. In a report— “The Sprawling Reach of Complex threats” released by TrendMicro, around 61,132,338 ransomware-related attacks were recorded in 2019 as compared to 55,470,005 attacks in 2018.17
“Covidlock”— another ransomware disguised as a COVID-19 tracking application and had crippled the computer systems worldwide. In its working, CovidLock instantly downloads a ‘file-encrypting’ malware from a website, disguised as WHO, onto the targeted device(s) and then lock the data until a USD 100 ransom is paid in Bitcoin (BTC).18 Upon failure to agree with the terms and conditions of CovidLock within 48 hours, the malware deletes all images, contacts, messages, and videos stored on the device.
In India, one of the leading technologies and consulting companies—Cognizant was targeted by the ransomware attack. Cognizant confirmed that in a security incident on 17 April 2020, the internal systems were affected and service disruption to some of their clients worldwide, was caused by “Maze” ransomware attack. The attackers held the data of victims as hostages threatening to leak the data if the target does not agree to pay the ransom amount.19 Maze ransomware seems to be a worrisome as apart from encrypting the data; it spreads over the network and affects other computers too in its path.
Zoom Meeting Client: A Privacy Disaster
The lockdown situation has moved several individuals to conduct online meetings, both work-related and private, via ‘Zoom Meeting client’— a teleconferencing software-based conference room solution used around the world. According to a research survey at the end of December 2019, the registered users (paid and free) on Zoom application (hereafter app) was approximately 10 million. However, in March 2020, the number of daily Zoom meeting participants skyrocketed and reached more than 200 million registered users.20 The high-rated usage of Zoom comes with security-related concerns. Taking advantage of Zoom’s over-usage, cybercriminals have created fake and malicious domains and files associated with the Zoom app. According to a research by Check Point Software Technologies, since January 2020, more than 1700 new [malicious] domains were registered including the name “Zoom” and 25 per cent out of them were registered during the lockdown period, i.e. 23-29 March 2020. 21 It cannot be ruled out that cybercriminals may sell out the personal information captured through Zoom application, on the darkweb platform. On 01 April 2020, a Cyber Intelligence firm Cyble identified free Zoom IDs/accounts had been posted on hacker forums in Darkweb. Over 500,000 Zoom accounts were sold for less than a penny or some for free of cost.22
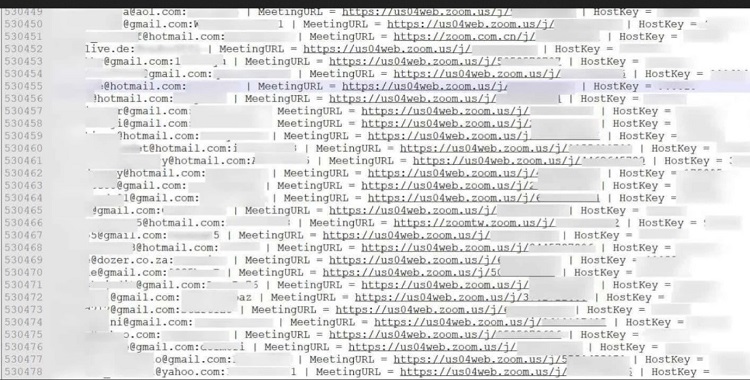
Image 3: Screenshot of compromised Zoom accounts sold over hacker forums on Darkweb. [Source: GizChina.com]
The researchers at Cyble recommended users to tighten the security settings on the application and remain cautious of unsought messages and e-mails. Another significant security concerns in Zoom app was the “Zoom Bombing” in which uninvited participants may view the proceedings of the meeting and at worse could share the pornographic content. Several schools, organisations had been the victim of the Zoom bombing in the past few weeks. On 30 March 2020, India’s Computer Emergency Response Team (CERT-In) issued an advisory— CIAD-2020-0010 regarding the “Secure usage of Zoom video conferencing application”. The advisory highlighted the vulnerabilities, including Zoom bombing, and advised measures to reduce the risks and attacks emerged from the vulnerabilities within the application.23 Subsequently, on 02 April 2020, CERT-In issued another advisory— CIAD-2020-0011, highlighting the multiple vulnerabilities exposed in Zoom app which could give elevated privileges, such as information disclosure, UNC Path Injection, to the cyber-attacker to obtain the sensitive information on the targets’ system.24 Considering the security threat on the usage of Zoom client, the Ministry of Home Affairs (MHA) issued an advisory on 16 April 2020, stating that the “platform is not for use by the Government officers/officials for official purposes”.25 The advisory referred to earlier advisories issued by the CERT-In with the guidelines to safeguard individuals who would like to use the Zoom client for private purposes.
Likewise, Delhi Police’s Cyber Crime Cell has tweeted the “suggestions on Zoom usage” on their twitter handle (@DCP_CCC_Delhi).26 The suggestions included:
- Avoid sharing meeting link on Social Media or Public Forums.
- Avoid using Personal Meeting ID (PMI) to host public meetings, instead use randomly generated IDs.
- Enable the “waiting room” feature to stop unwanted invitees from joining the meeting until the host’s approval.
- Enable the “Host Only” option to share screens.
- Enable settings to allow only registered and authenticated users to join meetings.
- Prevent transfer of files by disabling “File Transfer” feature so that malicious files cannot be shared.
- “Lock” Zoom meeting room once all participants joined in.
Online Child Sexual Abuse (CSA)
As a disturbing and dark side of the lockdown scenario, the paedophiles became more active in a lookout for the child pornography material online, especially on porn sites such as PornHub. Some international organisations such as the Europol, the United Nations, and the ECPAT (End Child Prostitution and Trafficking) International has reported that during the lockdown period there has been an increase in the demand for and availability of the Child Sexual Abuse Material (CSAM)27; and various other forms of online Child Sexual Abuse (CSA) activities such as cyber-grooming and sexual coercion. It is highly likely that paedophiles and child sexual abusers may have migrated to the Internet, and due to the absence of stringent laws-led actions against online CSAM, there will be a rise in CSA activities.
The Special United Nations Human Rights representatives— Maud de Boer-Buquicchio and Najat Maalla M’jid have warned that in addition to the travel restrictions imposed during the lockdown, the rise in online users shall “spike in online sexual grooming by paedophiles and sexual predators, live streaming of child sexual abuse and the production & distribution of CASM”.28 To make social distancing and lockdown a success, the adult porn site— PornHub had made the ‘premium’ adult content freely available to people worldwide under the category of “stay home” since 24 March 2020. 29 Citing the data from PornHub, the India Child Protection Fund (ICPF) reported that during the lockdown period in India, the web traffic on PornHub hiked by 95 per cent within a week (as highlighted in the Image 1), in comparison with the web-traffic pre-COVID-19.30
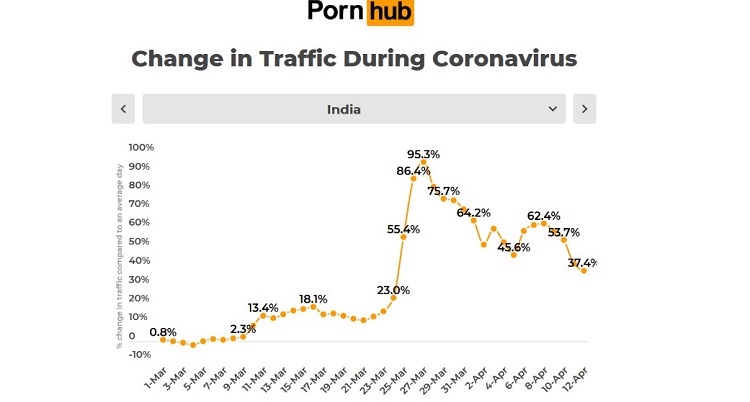
Image 4: Change in PornHub’s web-traffic from India from 01-March to 12 April [Source: PornHub Insights]
As highlighted in the Image 1, the percentage change to average daily web traffic from India was 18.1 per cent on 17 March, but it spiked from 23 per cent to 95.3 per cent from 24-31 March 2020. Even though India has banned pornography, the consumption of child sexual exploitation content is still one of the biggest challenges. Likewise, other cybercriminals, paedophiles have used the Internet in “incognito” mode using the Virtual Private Network (VPN) to evade the ban on CASM imposed by the Government of India (GoI). In a report by the ICPF which cites data from PornHub, an increase in search has been recorded for keywords such as “child porn”, “sexy child”, and “teen sex videos”. 31 During the initial 11-day lockdown (20-31 March 2020), the government-supported “Childline India” helpline received 3.07 lakh calls, out of which 30 per cent (92,105) calls were about requesting child protection from various forms of abuse and violence.32 Promoting the best practices to counter CSA activities in the digital world, the Minister of Women and Child Development— Smriti Irani, on 14 April 2020, has tweeted that “all child helplines are alerted to reach out in all districts for not only emergency support but also to report such abusive material to local administration and police”.33
Dissemination of Fake News
In the ongoing situation, the fake stories or news about COVID-19 pandemic are being labelled as “infodemic”. At the Munich Security Conference held on 15 February 2020, the Director-General of the World Health Organisation (WHO)— Tedros Adhanom Ghebreyesus emphasised that:34
The dissemination of incorrect information over social-media platforms powered by the Internet may cause serious impact on the citizens of any country. As its name suggests, Fake news consists of incorrect, and sometimes harmful information which can adversely affect the public health response to the situation and may incite a social disorder, further leading to a law & order situation in the targeted area. During the first phase of lockdown (25 March to 14 April 2020), the government of Maharashtra had issued an advisory explaining “Dos and Don’ts” regarding the rumours spread during the COVID-19 pandemic.35 Similar to the tunes, to tackle the infodemic, Assam police registered 52 cases in which 25 people were arrested for spreading fake news over social media and instant messaging applications. Under the guidelines issued by the relevant ministries, the Cyber Cell and police forces are ensuring that no rumour or fake newsmonger is left unpunished.36
As “several lies may appear as a tiny truth”, fake news as a mixture of much incorrect information may appear as a piece of “real” information, challenging the intellect of an individual and making it difficult to find what is right and accurate in the story. Since it is shared by an individual’s trusted source (friends and family members), the person may likely share it further without reading the complete story or try to find if it is authentic. In the case of COVID-19, the uncertainty among people is leading them to trust on the misinformation or fake news.
Keeping “Cyber Safe” During Lockdown
The Government of India (GoI) has timely issued several advisories for its citizens to stay safe during the pandemic COVID-19. Similarly, to tackle the cyber-attacks during the lockdown situation, the concerned authorities and agencies have issued cyber-safety advisories to educate citizens to maintain cyber-hygiene and stay safe from cyber-attacks. To promote the best cyber safety practices during the chaos of COVID-19, the Ministry of Home Affairs (MHA), jointly with the National Cybercrime Coordination Centre (NCCC) issued “Cyber Security” tips to consider while using computers/digital devices while doing ‘work-from-home’. The MHA has urged citizens to use the laptop provided by the workplace, instead of using personal, if applicable. It shall be best to use digital devices for work and entertainment purposes separately.37
In a telephonic interview with ET Online, India’s National Cyber Security Coordinator (NCSC)— Lt Gen Rajesh Pant warned the cybercriminals not to take advantage of the lockdown situation and work-from-home scenario for carrying out cyber-attacks on individuals and enterprises.38 The Prime Minister’s Relief Fund against COVID-19— “PMCares@sbi” was also targeted; cybercriminals created malicious websites and mobile applications using similar keywords to lure the people. On 29 March 2020, Delhi Police’s DCP Cyber Crime informed that cybercriminals had created a fake UPI (Unified Payments Interface) ID “Pmcare@SBI” which was identified and subsequently blocked.39
Tackling Fake News
Unfortunately, in comparison to the rapid spread of fake news, only handful measures are in action to identify if distributed information is real or fake. On analysing, a piece of fake news would likely consist of information which could be more surprising, sometimes upsetting and tend to trigger anger or anxiety in the recipient or reader.40
Image 5: “Fake News Verification” module highlighted on the Delhi Police website. [Source: delhipolice.nic.in]
On 06 April 2020, Delhi Police had launched a “Fake News Verification Module” on their website portal. Through this module, citizens can report of any suspected fake news via uploading the content of its further investigation and clarification. Further, a piece of information which seems fake shall be double-checked from other sources of information; one of them is reputable news services. To cross-check the information tweeted from a Twitter account/handle, ‘Botometer’ designed by the Indiana University41 classifies the Twitter account/handle as a ‘Bot’ or ‘human’ by examining the profile, social network structure, temporal activity, language used, and sentiment. On the scale of 0-5, the higher the score, the more likely that the account is a ‘Bot’. Botometer fights false information by identifying bots, which are a frequent source of misinformation, and their content.42 An individual may also cross-check the fake news on “fact-check” websites, such as ALT News (https://www.altnews.in/), FactCheck (https://www.factcheck.org/), and Snopes (https://www.snopes.com/), which highlight mostly circulated fake news or stories.
Dealing with Ransomware & Malware Attacks
Putting on the safeguards against the malware and ransomware attacks, the Data Security Council of India (DSCI), established by NASSCOM jointly put up efforts to respond to security challenges via sharing learning and best cyber practices. Specifically, on the threat of Maze ransomware, the DSCI has issued an advisory to keep the vigilance against such attacks. Some of the recommendations included:43
- Strengthening e-mail security to detect harmful attachments. Using e-mail application with in-built security solutions.
- For home users, it is essential to install and update the Internet Security Solution products, such as Kaspersky, Norton, AVG, which area having in-built detection and protection from Ransomware and Malware attacks.
- Effective Data Back-up policy.
- Follow-up of best practices while granting system access to the files.
Ensuring the Operating System is up to date with issued updates from the vendor. The Security application shall do vigilant monitoring of remote access granting systems.
As mentioned earlier, the malicious COVID-19 FAQs related applications can be used as a backdoor to install malware/ransomware or to instigate phishing attack. As a counter-measure to such attacks, the Government of India developed a mobile application— Aarogya Setu, which aimed at educating the users regarding risks, best practices, and provide relevant advisories about the containment of COVID-19.
Image 6: “AarogyaSetu” Application shown at MyGov portal [Source: www.mygov.in]
On 19 March 2020, a global coalition to fight against cybercriminals was constituted having around 2,700 cybersecurity experts worldwide, including 10 Indians, together on the common virtual platform— “COVID-19 Cyber Threat Coalition (CCTC), to tackle cyberattacks centric to COVID-19 theme. The chief scientist of the Sophos Labs— Joshua Saxe coordinates the CCTC network of experts.44 The primary objective of this coalition was to instantly disseminate the information about ongoing cyber-attacks and suggesting an environment or framework to an organisation to swiftly defend their assets against the attack by taking down offending websites or IPs (Internet Protocols).
Conclusion
In the unfortunate time of pandemic COVID-19 worldwide, the cybercriminals are not sparing the individuals and enterprises but taking advantage of less secured cyber environment in which employees are doing work-from-home and also using Internet services for private use. It is essential for every individual to understand the seriousness of the “unsafe” cyber environment and to be aware of online threats such as phishing scams, malicious links or websites. Conveniently, cybercriminals are luring random people through e-mails, text messages or social media platforms to enter their details on fake websites and obtain the credentials and other confidential information, which they can use against the victim against ransom. Under the phenomenon of cyber-hygiene, deployment of competent and reliable anti-virus or Internet security software, regular update of the Operating System (OS), and other Software installed on the computer system shall be a regular practice to keep guards against the cyber-attacks. On 30 August 2019, the Government of India, under the Ministry of Home Affairs, had launched the “National Cyber Crime Reporting Portal” (https://cybercrime.gov.in/), which is one of the best initiatives to facilitate cyber-victims in reporting cybercrime complaints online. The portal also provides useful resources such as “Cyber Safety Tips”, “Cyber Awareness” and “Citizen Manuals”. Through collaborative efforts of the government, enterprises, and people, through awareness and measures against the cyber threats, a secured cyber environment would server as value addition in the development of a nation.
Endnotes
- Kevin D Mitnick and William L Simon. The Art of Deception: Controlling the Human Element of Security (Indianapolis: Wiley Publishing Inc), 2002, p.3
- “Covid-19 Tracker”, Microsoft Bing, Available from: https://www.bing.com/covid
- Ibid. ;Note: Total COVID-19 cases= Active cases+Recovered cases+Fatal Cases. For example: As of 23 April 2020 (2249 hrs), total COVID-19 cases in India counts to 21,700, including 16,689 active cases, 4,325 recovered cases and 686 Fatal cases.
- “Lockdown”, Cambridge Dictionary, Available from:
https://dictionary.cambridge.org/dictionary/english/lockdown - Jeffrey Gettleman and Kai Schultz. “Modi orders 3-week total lockdown for all 1.3 billion Indians”, The New York Times, 24 March 2020, Available from: https://www.nytimes.com/2020/03/24/world/asia/india-coronavirus-lockdown.html
- “PM Modi extends national lockdown till May 3, next one week crucial in Covid fight”, The Economic Times, 14 April 2020, Available from: https://economictimes.indiatimes.com/news/politics-and-nation/pm-modi-extends-national-lockdown-till-may-3/articleshow/75133926.cms?from=mdr
- Manjeet Singh Negi. “close schools, all religious activities, extend lockdown: States tells Centre”, India Today, 07 April 2020, Available from: https://www.indiatoday.in/india/story/close-schools-all-religious-activities-extend-lockdown-states-tell-centre-1664354-2020-04-07
- Abhirup Roy and Nupur Anand. “Scammers try selling world’s tallest statue as pandemic boosts India’s cyber crime”, Reuters, 07 April 2020, Available from: https://www.reuters.com/article/us-health-coronavirus-india-fraud/scammers-try-selling-worlds-tallest-statue-as-pandemic-boosts-indias-cyber-crime-idUSKBN21P0KH?
- Reuters. “Police in India catch scammers trying to sell world’s largest statue for $4 billion”, New York Post, 07 April 2020, Available from: https://nypost.com/2020/04/07/scammers-try-selling-worlds-tallest-statue-as-pandemic-boosts-indias-cyber-crime/
- “NortonLifeLock Cyber Safety Insights Report”, Norton, Available from: https://us.norton.com/nortonlifelock-cyber-safety-report
- “Top 5 social media scams”, Norton, Available from: https://in.norton.com/internetsecurity-online-scams-top-5-social-media-scams.html
- Brijesh Singh. “Coronavirus Pandemic is proving to be a boon for cyber criminals”, The Quint, 18 April 2020, Available from:https://www-thequint.com.cdn.ampproject.org/c/s/www.thequint.com/amp/story/voices%2Fopinion%2Fcoronavirus-covid-19-cyber-crime-fraud-fake-domain-name
- Tarun Sharma. “Coronavirus pandemic | No locking down cyber crime, Maharashtra sees a 25% spike in two weeks”, Money Control, 07 April 2020, Available from:
https://www.moneycontrol.com/news/india/coronavirus-pandemic-no-locking-down-cyber-crime-maharashtra-sees-a-25-spike-in-two-weeks-5115421.html - AFP. “Internet oversees seek crackdown on coronavirus website scams”, Barron’s, 07 April 2020, Available from: https://www.barrons.com/news/internet-overseers-seek-crackdown-on-coronavirus-website-scams-01586284806
- Ryan Gallagher and Bloomberg. “hackers without conscience demand ransom from dozens of hospitals and labs working on coronavirus”, Fortune, 01 April 2020, Available from: https://fortune.com/2020/04/01/hackers-ransomware-hospitals-labs-coronavirus/
- “New variants of Russian mobile banking trojan Riltok go international”, Kaspersky, 25 June 2019, Available from: https://www.kaspersky.com/about/press-releases/2019_new-variants-of-russian-mobile-banking-trojan-riltok-go-international
- “The Sprawling reach of complex threats”, Trend Micro, 25 February 2020, Available from: https://www.trendmicro.com/vinfo/us/security/research-and-analysis/threat-reports/roundup/the-sprawling-reach-of-complex-threats
- Naveen Goud. “Details of CovidLock ransomware and Czech hospital infection”, Cybersecurity Insiders, Available from: https://www.cybersecurity-insiders.com/details-of-covidlock-ransomware-and-czech-hospital-infection/
- TNN. “Cognizant comes under ‘Maze’ ransomware attack”, The Times of India, 20 April 2020, Available from: https://timesofindia.indiatimes.com/business/india-business/cognizant-comes-under-maze-ransomware-attack/articleshow/75239553.cms
- Eric S Yuan. “A Message to Our Users”, Zoom-Blog, 01 April 2020, Available from: https://blog.zoom.us/wordpress/2020/04/01/a-message-to-our-users/
- “COVID-19 Impact: Cyber Criminals Target Zoom Domains”, CheckPoint Software Technologies, 30 March 2020, Available from: https://blog.checkpoint.com/2020/03/30/covid-19-impact-cyber-criminals-target-zoom-domains/
- Lawrence Abrams. “Over 500,000 Zoom accounts sold on hacker forums, the dark web”, Bleeping Computer, 13 April 2020, Available from: https://www.bleepingcomputer.com/news/security/over-500-000-zoom-accounts-sold-on-hacker-forums-the-dark-web/
- Government of India- Ministry of Electronics and Information Technology. “Secure usage of Zoom video conferencing application— CIAD-2020-0010”, Indian Computer Emergency Response Team (CERT-In), 30 March 2020, Available from: https://www.cert-in.org.in/s2cMainServlet?pageid=PUBVLNOTES02&VLCODE=CIAD-2020-0010
- Government of India- Ministry of Electronics and Information Technology. “Multiple vulnerabilities in Zoom video conferencing application— CIAD-2020-0011”, Indian Computer Emergency Response Team, 02 April 2020, Available from:
- Government of India- Press Information Bureau. “MHA issues advisory on Secure use of Zoom meeting platform”, Ministry of Home Affairs, 16 April 2020, Available from: https://pib.gov.in/PressReleaseIframePage.aspx?PRID=1615008
- DCP Cybercrime (@DCP_CCC_Delhi). 2020. “Suggestions on Zoom Usage”. Twitter, 02 April 2020, 04:55 PM, Available from: https://twitter.com/DCP_CCC_Delhi/status/1245673639132844033
- “Why children are at risk of sexual exploitation during COVID-19”, ECPAT International, 07 April 2020, Available from: https://ecpat.exposure.co/covid19 ; “Coronavirus: Online child abuse warning during lockdown”, BBC News, 27 March 2020, Available from: https://www.bbc.com/news/technology-52067507
- “Children vulnerable to abuse and violence during coronavirus lockdowns, UN experts warn”, United Nations News, 07 April 2020, Available from: https://news.un.org/en/story/2020/04/1061282
- “Pornhub is giving out ‘free premium’ to encourage people to stay at home amid corona lockdown”, News18, 25 March 2020, Available from: https://www.news18.com/news/buzz/pornhub-is-giving-out-free-premium-to-encourage-people-to-stay-at-home-amid-corona-lockdown-2550601.html
- Ambika Pandit. “ICPF report warns of sharp rise in demand for online child pornography during lockdown”, The Times of India, 14 April 2020, Available from: https://timesofindia.indiatimes.com/india/icpf-report-warns-of-sharp-rise-in-demand-for-online-child-pornography-during-lockdown/articleshow/75127399.cms
- Hemani Sheth. “India lockdown: Online child pornography consumption spikes by in India, says ICPF”, The Hindu-Business Line, 14 April 2020, Available from: https://www.thehindubusinessline.com/info-tech/india-lockdown-online-child-pornography-consumption-spikes-by-in-india-says-icpf/article31337221.ece#
- PTI. “Coronavirus lockdown | Govt. helpline receives 92,000 calls on child abuse and violence in 11 days”, The Hindu, 08 April 2020, Available from: https://www.thehindu.com/news/national/coronavirus-lockdown-govt-helpline-receives-92000-calls-on-child-abuse-and-violence-in-11-days/article31287468.ece
- Smriti Z Irani (@smritiirani). 2020. “We have worked with @BBAIndia…….to local admin & police”. Twitter, 14 April 2020, 04:03 PM, Available from:
https://twitter.com/smritiirani/status/1250009325696843776 - Speech by the WHO Director-General Ghebreyesus at the Munich Security Conference. World Health Organisation, 15 February 2020, Available from: https://www.who.int/dg/speeches/detail/munich-security-conference; Rohini Mohan. “Coronvirus: Fake News keeping pace with speed of Covid-19 in India”, The Straits Times, 24 March 2020, Available from: https://www.straitstimes.com/asia/south-asia/coronavirus-fake-news-keeping-pace-with-spread-of-covid-19-in-india
- Vidya. “Coronavirus: Maharashtra registers 115 cases over fake news since lockdown”, India Today, 07 April 2020, Available from: https://www.indiatoday.in/india/story/coronavirus-maharashtra-registers-115-cases-over-fake-news-since-lockdown-1664318-2020-04-07
- Tulika Devi. “Assam Police fights coronavirus ‘infodemic’:52 cases registered, 25 people arrested for spreading fake news, 110 sent for counselling”, First Post, 08 April 2020, Available from: https://www.firstpost.com/health/assam-police-fights-coronavirus-infodemic-52-cases-registered-25-people-arrested-for-spreading-fake-news-110-sent-for-counselling-8241161.html
- “Home Ministry suggests cyber security tips for people working from home”, The Hindu, 11 April 2020, Available from: https://www.thehindubusinessline.com/info-tech/home-ministry-suggests-cyber-security-tips-for-people-working-from-home/article31315665.ece#
- Sandhya Sharma. “Cyber chief’s warning as hacker’s target PM’s Covid fund”, Economic Times, 31 March 2020, Available from: https://economictimes.indiatimes.com/tech/internet/cyber-chiefs-warning-as-hackers-target-pms-covid-fund/articleshow/74877953.cms
- Ibid.
- Melissa De Witte. “People’s uncertainty about the novel coronavirus can lead them to believe misinformation, says Stanford scholar”, Stanford News, 16 March 2020, Available from: https://news.stanford.edu/2020/03/16/fake-news-coronavirus-appealing-avoid/
- Indiana University. “Botometer”, Available from: https://botometer.iuni.iu.edu/#!/
- “Botometer”, RAND Corporation, Available from: https://www.rand.org/research/projects/truth-decay/fighting-disinformation/search/items/botometer.html
- “Maze Ransomware: NASSCOM-DSCI Advisory”, DSCI, Available from: https://www.dsci.in/sites/default/files/Maze_Ransomware_Advisory.pdf
- Sushovan Sircar. “As COVID-linked Cyber attacks surge, a global IT Army fights back”, The Quint, 07 April 2020, Available from: https://www.thequint.com/tech-and-auto/indians-part-of-global-cyber-threat-coalition-fight-coronavirus-covid-19-cyber-attacks
(The paper is the author’s individual scholastic articulation. The author certifies that the article/paper is original in content, unpublished and it has not been submitted for publication/web upload elsewhere, and that the facts and figures quoted are duly referenced, as needed, and are believed to be correct). (The paper does not necessarily represent the organisational stance... More >>
Image credit: Anurag Sharma











Post new comment