USA is not new to the controversies related to surveillance of its own citizens as well as its allies. Neither is Project PRISM a first such surveillance project nor is Snowden first such whistle-blower. US intelligence agencies have worked on many projects which precedes PRISM (US-984XN). Some of them are Carnivor, DSCNet, Naruslnsight, Total Information Awareness, ADVISE, Trailblazer, ThinThread, Mainway, Turbulence, Stellar Wind, Echelon, Dropmire and Tempora. Many of these projects being unconstitutional were stalled by the US Congress/Senate. Though discontinued, the software, concepts and project teams of some of the defunded projects were redeployed for newer versions. According to reports, PRISM is presently collecting more than 1 billion records a day from E-mails, social networks, Skype, Google, Microsoft, Blog entries, telephone service providers, websites, and this data is dumped at one place. Thereafter this data is normalized, co-related, aggregated, and analyzed for preparing appropriate threat reports. Please see a series of images below the article as to how users are forced to authorize to give away their personal information and also allow the application to call other phones or send SMS on their behalf and without their permission. The example is of Twitter application but same is true for most of other applications.
There are two facets of PRISM controversy; one is breach of Constitution and laws of US itself; and second is information gathered from other countries. The Indian Government should not concern itself with the former. However, the latter issue is serious for our national security and international relations.
According to the US government, the data collected are only metadata. Metadata means only header information of an Internet Protocol (IP) packet (not the data), E-mail addresses and its header (not the content), telephone call detail records (not the voice), etc. The US government further claims that contents of these communications were not gathered en-masse. In other words, it implies that for specific targets content information is also gathered.
It is important to understand the concept of privacy and if compromised its adverse effects. Privacy issues are only valid for gathering personal information by own government because the state and its officials can abuse the private information for political purpose or/and harassing citizens for personal benefits. As foreign states cannot abuse the private information of an average citizen, it is fallacy to presume that such information is in breach of privacy unless this information is shared back with the government of the concerned citizen or a marketer. However, private information of influencers, decision makers and corruptible government officials can be abused by foreign powers against our national interest. Despite the fact that information collated through project PRISM could have identified terrorist modules and Hawala operatives in India, but as India’s National Security Advisor has stated despite such knowledge and also protocols in place, USA did not share such information even at the time of crisis.
Additionally information can be gathered if a project like PRISM has the capacity, albeit with the help of companies like Google and Microsoft to ex-filtrate information from government networks as well as networks of influential private organizations. According to Reuters, US government through seed fund companies such as In-Q-Tel has planted backdoors and spyware in the computers purchased by governments of some Asian countries.
In project PRISM whether the government of USA has breached its constitution and laws is an internal matter of the USA and it is up to the citizens of USA to decide as to s how do they want to take this matter forward. Though many countries may retaliate by instigating US citizens against their own country as US has done to others on more than one occasion. But India should keep out of the internal matter of that country. The point of concern for India is breach of the Vienna Convention.
According to the Vienna Convention on Diplomatic Relation, Article 27 guarantees free communication between a mission and its sending State by all appropriate means, and ensures that the diplomatic bag carrying such communications may not be opened or detained even on suspicion of abuse. Given the purposes of diplomatic missions, secure communication for information and instructions is probably the most essential of all immunities.
US President Barack Obama has shrugged off such allegation by saying that allies often spy on each other. If this becomes an accepted norm and stated policy of the most powerful nation, in total contravention of the Vienna Convention, then it is going to be down slope from here onward in international relations and the world order. USA has been tinkering with various international conventions for some time. The issue here is that Mr Obama maybe telling the truth but a formal statement coming out from the mouth of a President becomes a stated policy and amounts to brazen breach of Vienna Convention.
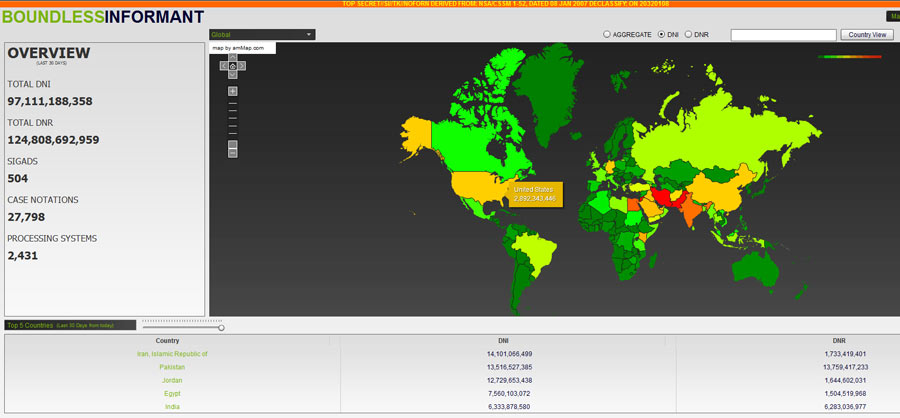
The Heat map published (figure 1) by ‘The Guardian’ news paper shows that India was the 5th largest surveillanced country for top secret information and was placed after Iran and Pakistan. Another disturbing fact which emerged is that India is one of the 38 countries whose embassies were snooped by the US. One of the slides of PRISM leaked to the the Guardian newspaper shows the reason as to why USA adopted the means to exploit this project. According to figure 2, about 85% of world’s internet traffic flows through the territory of USA. Additionally, all important servers such as primary domain name resolution servers and internet exchanges are located under the control of the US Department of Commerce. This forces practically most of the countries to send their data to USA for processing. Several attempts to extract these servers and important internet organizations out of the clutches of US government have failed. This provides huge asymmetry in favor of USA and the Americans have breached this trust. The situation is similar to as that of haves and have nots or akin to the relationship between a landlord and landless laborers. The problem becomes complicated when the landlord refuses to comply with the signed agreement as in this case the Vienna Convention.
Apparently, China has identified this threat from USA to exploit its big companies like Google, Facebook, Twitter, Microsoft, etc. For this reason, China not only deployed the great firewall but also has come up with its own version of Twitter and Facebook. Google has been thrown out, while source code of Microsoft is in possession of Chinese government. Hence a perfect defense has been set up by China. And in counter offensive, where USA ex-filtrated information by forcing the user to sign the terms and conditions of US companies, China deployed complex web of spywares across the internet.
India must understand that in the case of information security, there is need to comprehend as to what is happening and this being a complex techno-military-diplomatic issue, an average bureaucrat cannot provide leadership. A group of professionals is required. Recently released cyber security policy, though faulty at many places, requires to be implemented on priority and funds required for the same have to be released on an urgent basis.
There are lessons to be learnt in successful stealing of information by Snowden (internal threat) from the sensitive networks of US National Security Agency (NSA). There were the following lacunae in the Information Security Management of NSA, which enabled this theft.
a. Information security standard NIST 800-53 was not complied with.
b. The data was not kept encrypted and Snowden could have free visibility.
c. There was no regular log analysis.
d. Data loss prevention mechanisms were not implemented / monitored.
e. Power of Active Directory not exploited to exercise access control
f. No redaction (masking of personally identifiable information (PII)) was undertaken.
g. Trip wires and audit trails were not set appropriately to activate alarms.
h. And most importantly NSA, US had not subjected itself to third party information security audit.
It is impossible to protect metadata analysis on the internet if the packets passed through a sniffing server. However, in 2004, realizing this very problem that every packet was getting routed to USA, India had established internet exchanges (NIXI) and few root servers within the country. Sadly, the government of India has failed to mandate the national gateway providers that they should use NIXI instead of US based internet exchanges. Consequently, not only large number of IP packets are still being routed through US but also NIXI, a national asset, is financially poorer. If such a response is continued, then the government may decide to shut down NIXI thereby forcing all packets which should have stayed within the country, to once again be routed through US. It is, therefore, necessary that the government pass necessary orders mandating national gateway providers to use NIXI. Importance of NIXI and root servers must be realized.
The National Cyber Security Policy envisages requirement of about five lakh information security professionals. However, according to a report, there are less 500 hundred such people in the government. The Department of Information Technology had prepared curriculum for B.Tech and M.Tech in Information Security few years ago. This should be implemented immediately.
Glamorization of hacking has caused skew in the availability of information professionals. Most of the youngsters are pursuing so called ethical hacking courses. However, there is an equal need for professionals in log analysis, cyber forensics, application security, website security, network security, malware analysis, artifact analysis, cyber lawyers, incident handlers, risk analysts and information security auditors.
There can be no effective cyber security without effective tools and techniques. Presently, most of the information security providers use freeware cyber security tools and such freeware have their own limitations. The paid versions cost few lakhs of rupees and there are no Indian tools. CDAC, Thiruvananthapuram, had developed cyber forensic tools but over a period of time, it is not able to catch up with the changing technology.
If India desires to create its own Twitter or Facebook equivalent websites (which Big Adda and many such sites attempted), then it is critical that Indian languages are used extensively. There are no good software for voice to text and text to voice and handwriting recognition for Indian language. Presently Indian languages have keyboards which are similar to English keyboard, these keyboards are not intuitive to Indians and they have to think in local language than its equivalent English language and once again local language. This is not only a deterrence in use of computer by rural population but also will cause the death of Indian Languages. It must be noted that Indian languages have structured alphabet unlike languages based on Roman script. Hence they are more adaptable to the computer. Despite this fact, there is hardly any spell check and grammar check software for Indian languages. It must be noted that presently the fastest growing languages on the internet are Arabic and simplified Chinese language.
Without denying the fact that India needs surveillance and offensive capabilities in cyberspace, there is far more urgent need to build defenses. Without securing own information infrastructure critical as well as not so critical, it will be suicidal to launch any kind of cyber offensive. It must be noted with great concern that India was 3rd most infected country by Stuxnet. Any cyber weapon such as Stuxnet can bring our manufacturing industry to a grinding halt including defense equipment manufacturing industry within minutes.
Most of the controlling systems of the Internet are under the control of the US government. India should join hands with other countries to get these servers out of the positive control of US government. Similarly, India should proactively participate in various Internet governance bodies (if a Babu cannot go, then nobody should go attitude must be curtailed). China has healthy presence in governing boards of such bodies. In fact, one of the significant share holders of Facebook is a person from Hong Kong.
There are far too many facets to information security than just surveillance and none of them can be left behind. It is therefore necessary that the mechanism of National Information Board should be revived. Some may say that National Information Board is too big and unwieldy and it is difficult to get so many Secretary rank officers together. However, it must be noted that this was an effective and functional organization under previous National Security Advisors Mr Brijesh Mishra as well as Mr. J N Dixit.




Published Date: 8th July 2013, Image Source: http://img.gawkerassets.com









Post new comment