National
Telecom equipment manufacturers respond enthusiastically to the design-led incentive programme
Indian Prime Minister (PM) Narendra Modi had outlined his vision of making India a self-reliant or Atmanirbhar nation. In line with the vision, in 2021, the Govt. of India launched the Production Linked Incentive (PLI) scheme to encourage telecom equipment manufacturing in the country. So far,31 companies are beneficiaries of the scheme for manufacturing various telecom equipment. In June 2022, the design-led PLI scheme was also introduced to advance the entire value chain in telecom manufacturing. All the existing incentives in the said scheme will be increased by 01 per cent. India is primed to become a telecom and networking equipment design and production centre.[1]
Ministry of Communication hosted ITU’s Regional Standardisation Forum for Asia and Oceania region in New Delhi, India
On 08 August 2022, the Ministry of Communication hosted the International Telecommunication Union (ITU)’s Regional Standardisation Forum (RSF) for Asia and Oceania region in New Delhi, India. The Forum focused on “Regulatory and Policy aspects of Telecommunications/ICT” and was followed by the four-day meeting of ITU-T Study Group 3 Regional Group Asia and Oceania (ITU-T SG3RG-AO) from 09th-12th August 2022. Minister of State for Communication Devusinh Chauhan inaugurated the RSF.
The Forum serves as a platform for the constructive exchange of ideas on issues related to standardisation, such as India's experience in various technological fields, such as Sustainable Digital Transformation (SDT), the function of ITU standards, utilising technology for financial and digital inclusion in emerging markets, the evolution of the data value chain, and digital health. The RSF was addressed by 15 eminent speakers from academia, international Organisations, the ICT sector and the Government of India (GoI). Over 250 delegates from 20 countries participated in the RSF. The key takeaways from the deliberations in the RSF will be presented atthe ITU-T Regional Group of Asia and Oceania meeting for further work on standardisation in the emerging areas.[2]
CERT-In hosted the Cyber Security exercise “Synergy” as part of the International Counter-Ransomware Initiative-Resilience Working Group
On 31 August 2022, the Indian Computer Emergency Response Team (CERT-In), in collaboration with the Cyber Security Agency (CSA) of Singapore, designed and conducted the Cyber Security exercise “Synergy” for 13 countries as a part of the International Counter-Ransomware Initiative-Resilience Working Group (ICRI-RWG), led by India under the leadership of National Security Council Secretariat (NSCS).
The exercise theme was “Building Network Resiliency to Counter Ransomware Attacks”. The exercise scenario was inspired by real-life cyber incidents in which a low-impact domestic ransomware issue developedinto a global cyber security disaster. The CERT-In sponsored the exercise "Synergy" on its exercise simulation platform. Each State sent a National Crisis Management Team (NCMT) comprised of several government entities such as National CERTs/CSIRTs, Law-Enforcement Agencies (LEAs), Ministry of Communication & IT, and security agencies.[3]
Reliance Jio will launch ‘World’s most extensive’ 5G services during the Deepawali festival
At Reliance Industries Limited (RIL)’s 45th Annual General Meeting (AGM), the company’s Chairman Mukesh Ambani announced that Jio would commence the world’s most extensive 5G services to its subscribers in metro cities in the next two months. “Jio 5G will be the world’s largest and most advanced 5G network. Jio will deploy the latest version of 5G, called standalone 5G, which has zero dependencies on the 4G network. Jio further announced that they are committed to making India a data-powered economy even ahead of the US and China,” Jio has emerged as the biggest investor by committing US$19 Billion on 5G Communication services including US$11 Billion on Airwaves.
Threat actors exploiting “Zimbra” Collaboration Suite Vulnerability
According to the Indian Computer Emergency Response Team (CERT-In),threat actors actively exploit an authentication bypass Remote Code Execution (RCE) vulnerability in Zimbra Collaboration Suite. The exposure enables the attacker to access the target network and launch additional attacks. The RCE vulnerability exists in the Zimbra collaboration suite due to improper uploading of files by the mboximport function. An authenticated attacker with admin rights could exploit this vulnerability by executing a specially crafted request to upload arbitrary files. Successful exploitation of the vulnerability could allow the attacker to traverse directories on the target system.[4]
CERT-In issued the “India Ransomware Report for H1-2022.”
On 02 August 2022, the Indian Computer Emergency Team (CERT-In) released a report titled "Indian Ransomware Report for H1-2022," which covered the most recent tactics and approaches and sector-specific trends detected in the first half of 2022 in the Indian Cyber Space.[5] The report also addressed ransomware-specific incident response, remediation, and mitigation techniques in light of the current threat scenario. The information is available at https://cert-in.org.in/PDF/RANSOMWARE_Report.pdf
International
An organisation in Eastern Europe became a victim of the most significant DDoS attack— 659 million Packets/Second
At the end of July and beginning of August 2022, an organisation became a victim of the biggest DDoS (Distributed Denial of Service) attack with traffic of 659 million Packets per second (Mpps). Akamai Technologies announced that on 21 July 2022, they detected and mitigated the most significant DDoS attack launched against a European customer on the Prolexic platform. The attack was massive, with globally distributed attack traffic at 853.7 Gbps (Gigabits per second) and 659.6 Mpps over 14 hours.
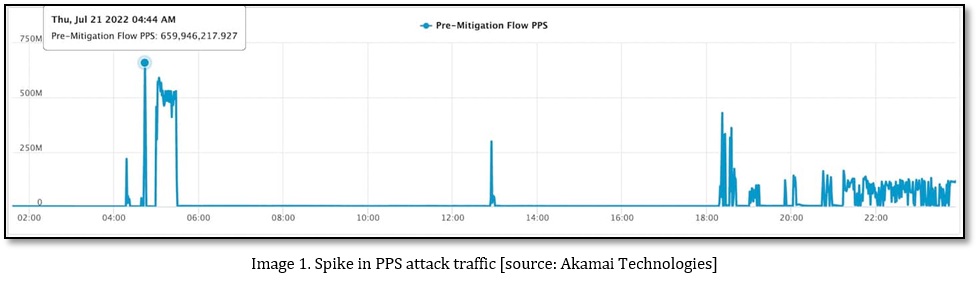
The victim based in Eastern Europe was targeted 75 times in the past 30 days with horizontal attacks consisting of UDP, UDP fragmentation, ICMP flood, RESET flood, SYN flood, TCP anomaly, TCP fragment, PSH ACK flood, FIN push flood, and PUSH flood, among others. In September 2021, Yandex— a Russian Internet company, was hit by the Meris botnet, which launched DDOS (Distributed Denial of Service) attacked with more than 21 million random packets. The use of DDoS attacks as a form of hacktivism has become increasingly popular in Eastern Europe due to incidents involving DDoS taking on a political tint.[6]
Chinese govt supported hackers deceptively carried out a year-long cyber espionage campaign against Australia
In a sophisticated year-long cyber espionage campaign, Chinese government-aligned hackers posed as media outlet employees and targeted Australian government agencies, news outlets, and manufacturing companies via the implantation of malicious software on targeted computers. In a phishing scam, these hackers claimed to be employees of Australian news publications, including The Australian and the Herald Sun.
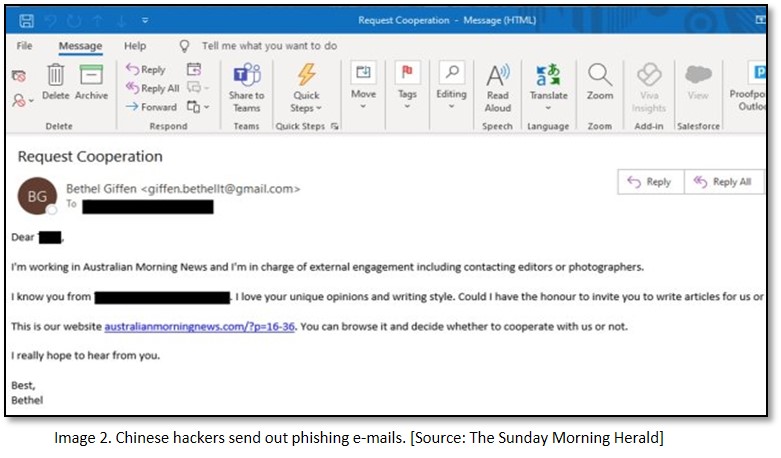
In the cyber espionage campaign, the hackers targeted an array of defence contractors, manufacturers, universities, government agencies and legal firms across the Asia-Pacific. According to a report prepared by PwC and Proofpoint— a US cyber security firm, a prolific China-based entity known as TA423 or ‘Red Ladon’ executed the cyber espionage operation. The group— TA423 has been operating since 2013. “China was using cyber-attacks to gain a long-term economic and military advantage over other nations,” said cyber security expert— Sherrod DeGrippo. The Chinese embassy in Canberra, Australia, Countering the claims, stated that “China always firmly opposes cyber-attacks and cyber theft in all forms. All such accusations are groundless.”[7]
Hackers increasingly exploited DeFi bugs to steal cryptocurrency: FBI
In a statement released, the Federal Bureau of Investigation (FBI) warned investors about the cyber-criminals' increasingly involvement in exploiting security vulnerabilities in Decentralised Finance (DeFi) platforms to steal cryptocurrency. The FBI encouraged investors to contact the FBI via the Internet Crime Complaint Centre (IC3) or the local FBI field office in case of any such theft. According to an estimate, around USD 1.3 billion in cryptocurrency was stolen between January and March 2022, stealing almost 97 per cent of it from DeFi platforms.
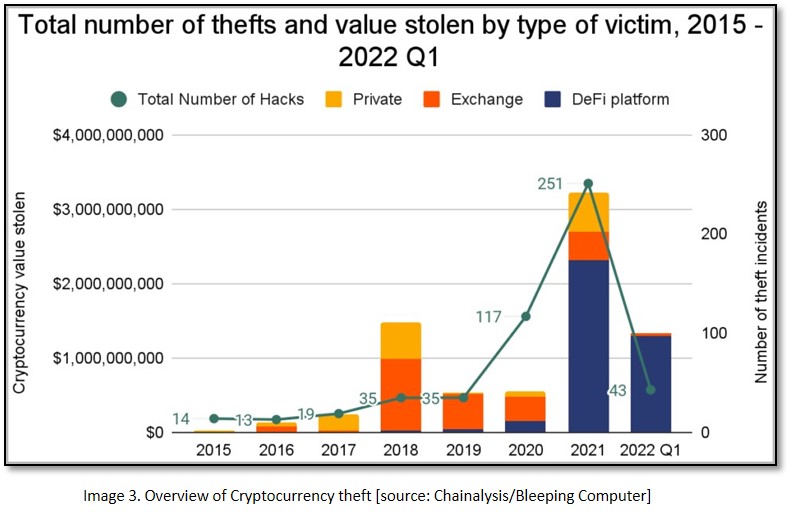
Attackers have utilised various ways to hack and steal cryptocurrency from DeFi platforms, including launching flash loans that trigger attacks in the platforms’ smart contracts and leveraging signature verification issues in its token bridge to withdraw all assets. The FBI has also observed hackers manipulating cryptocurrency price pairs by abusing a series of flaws, including the DeFi platforms’ use of a single price Oracle and then conducting leveraged trades to avoid slippage checks.[8]
Singapore witnessed a rise in cybercrime, phishing and ransomware threats in 2021
According to a report released by Singapore’s Cyber Security Agency (CSA), on 29 August 2022, firms and individuals faced a rise in cybercrime, phishing, and ransomware threats in 2021. In 2020, around 89 ransomware incidents were recorded; in 2021, the numbers jumped by 54 per cent, and 137 incidents were reported. Phishing cases also rose by 17 per cent in 2021, where about 55,000 unique Singapore-hosted phishing URLs with a “.sg” domain were observed; in 2020, around 47,000 such URLs were identified. “This was possibly driven by malicious actors’ exploitation of public interest in WhatsApp’s updated privacy policy announcement on users’ phone numbers being shared with Facebook,” informed the CSA. [9]
Endnotes :
[1] “Design led Incentive scheme gets enthusiastic response from Telecom Equipment manufacturers”, Ministry of Communications, 26 August 2022, available from: https://pib.gov.in/PressReleasePage.aspx?PRID=1854731
[2] “ITU’s Regional Standardisation Forum (RSF) for Asia and Oceania region to be inaugurated tomorrow by Shri Devusinh Chauhan”, Ministry of Communications, 07 August 2022, available from: https://pib.gov.in/PressReleasePage.aspx?PRID=1849356
[3] “CERT-In hosts Cyber Security Exercise ‘Synergy’ for 13 countries as part of International Counter Ransomware Initiative-Resilience Working Group”, Ministry of Electronics & IT, 31 August 2022, available from:https://pib.gov.in/PressReleasePage.aspx?PRID=1855771
[4] “Threat Actors exploiting Zimbra Collaboration Suite Vulnerability”, Indian Computer Emergency Response Team, 18 August 2022, accessed on 03 September 2022, available from: https://cert-in.org.in/
[5] “Indian Ransomware Report for H1-2022 by CERT-In”, Indian Computer Emergency Response Team, 02 August 2022, accessed on 03 September 2022, available from: https://cert-in.org.in/
[6]Sparling, Craig. “Largest European DDoS Attack on Record”, Akamai Technologies, 27 July 2022, accessed on 03 August 2022, available from: https://www.akamai.com/blog/security/largest-european-ddos-attack-ever
[7]Knott, Matthew. “Chinese hackers pose as Australian News Corp sites in cyber espionage scam”, The Sunday Morning Herald, 30 August 2022, accessed on 02 September 2022, available from: https://www.smh.com.au/politics/federal/chinese-hackers-pose-as-australian-news-corp-sites-in-cyber-espionage-scam-20220830-p5bduz.html
[8]Gatlan, Sergiu. “FBI: Hackers increasingly exploit DeFi bugs to steal cryptocurrency”, Bleeping Computer, 29 August 2022, accessed on 03 September 2022, available from: https://www.bleepingcomputer.com/news/security/fbi-hackers-increasingly-exploit-defi-bugs-to-steal-cryptocurrency/
[9]Ganesan, Natasha. “Singapore faced more cybercrime, phishing, and ransomware threats in 2021”, Channel News Asia, 29 August 2022, accessed on 03 September 2022, available from: https://www.channelnewsasia.com/singapore/cybercrime-ransomware-phishing-cybersecurity-2021-2906386

