NATIONAL
CERT-In issued advisory on Mobile-based Malware
On 30 May 2022, Indian Computer Emergency Response Team (CERT-In) issued advisory on mobile-based malware, along with methods and countermeasures. With the advent of smartphones and high-speed Internet connection, mobile accounts for more than 50 per cent of the Internet traffic worldwide, making it a worthwhile attack surface for cybercriminals.
The advisory included methods through which cybercriminals carried out activities, including fake applications, On-device fraud, Bypassing App store, fake calls, and where mobile-based malware are also using design practices like accessibility engines, infrastructure and C2 protocols that enable them to update their capabilities. Along with, the advisory also suggested countermeasures and best practices for users, including keeping OS (Operating System) and applications updated, use of strong authentication such as biometric and PIN, safe browsing practices, deleting data before discarding the device. [1]
Cisco Launched a tool of SMBs to assess Cyber Security Readiness
Cisco, on 26 May 2022, launched a cyber security tool for Small and Medium-sized Businesses (SMBs) based in Asia-Pacific region to assess their cyber security readiness amid of hybrid work environment. The tool’s concept is based on the premise that no attempt to access an organisation’s network architecture can succeed until trust is verified. As per Cisco’s cyber security for SMBs: Asia-Pacific businesses prepare for digital defense study, 62 per cent of Indian SMBs suffered cyber incidents in 2021 and cyber-attacks cost their business over ₹ 3.5 crore. Around 74 per cent SMBs also reported 85 per cent of customer information loss in cyber incidents.
“When a user accesses an application using a device, both the user and device are verified, with that trust continuously monitored. This helps secure the organisation’s applications and environments from any user, device, and location,” read the statement released by Cisco. The threat landscape for the SMBs becoming more sophisticated due to the digitisation at speed, therefore, securing their businesses is one of the top priorities for SMBs. “With new tool, the SMBs will ensure end-to-end protection across their workforce, and the workplace, with adoption of a zero-trust strategy to manage and strengthen their cyber security posture in a cloud-first world,” said Cisco India & SAARC’s Senior Director (System Engineering)— Anand Patil.[2]
The 7th Edition of India-Japan ICT Joint Working Group meeting recognised the importance of India-Japan Digital Partnership
On 13 May 2022, V L Kantha Rao (Additional Secretary, Department of Telecommunications, India) and Sasaki YUJI (Vice-Minister for Policy Coordination— International Affairs, Japan) virtually co-chaired the 7th edition of India-Japan ICT Joint Working Group (JWG) under the India-Japan ICT Comprehensive Cooperation Framework. Senior representatives from both governments and non-governmental stakeholders from industry, R&D, and Academia attended the meeting.
Recalling the India-Japan Summit held in March 2022, both sides recognised the need to strengthen the growing cooperation under India-Japan digital partnership, with a vision to enhance digital economy through promotion of joint projects for digital transformations. The JWG discussions were focused on enhancing further cooperation in various fields like 5G, Open RAN, Telecom Network Security, submarine cable systems, and Quantum Communications. [3]
Government of India proposed to set up India Data Management Office
Under the Digital India Corporation, India’s Ministry of Electronics and Information Technology (MeitY) will set up an India Data Management Office (IDMO), which will be responsible for framing, managing, reviewing, and revising the National Data Governance Framework Policy. The draft of the National Data Governance Framework Policy was released by the MeitY, seeking public comments on the draft till 11 June 2022.
The earlier version of the policy— India Data Accessebility and Use Policy had faced many criticism from experts, who believed that there was a lack of security safguards for anonymization, privacy infringement, and economic incentivisation. As per the draft of the data governance framework, the IDMO will design and manage the India Datasets platform which will in turn handle the requests of Indian researchers and start-ups which require access to non-personal or anonymised datasets. [4]
CERT-In issued discovery of Remote Code Execution (RCE) vulnerability in Apple products
On 20 May 2022, the Indian Computer Emergency Response Team (CERT-In) highlighted a Remote Code Execution (RCE) vulnerability in Apple watchOS, tvOS, and macOS, affecting Apple Watch, Apple TV, and Apple Mac systems. The vulnerability existed due to an out-of-bounds write issue in the AppleAVD component. Successful exploitation of this vulnerability may allow a remote attacker to execute arbitrary code with kernel privileges on the targeted system.[5]
INTERNATIONAL
Canada to ban China’s Huawei and ZTE from its 5G/4G networks
Following to the review by Canada’s independent security agencies and consultation with ‘closest’ allies, the Government of Canada decided to ban China’s Huawei and ZTE products and services from Canada’s 5G/4G communication networks. In a statement released on 19 May 2022, the Minister of Innovation, Science and Industry— Francois-Philippe Champagne has stated that “the Government of Canada is ensuring a long term safety of telecommunication infrastructure. As a part of that, the government intends to prohibit the inclusion of Huawei and ZTE products and services in Canada’s telecommunication systems.” [6]
As per the decision, the companies that already using the Huawei and ZTE equipment installed in their networks would be required to cease its use and remove it. The implementation of these measures are part of a broader agenda to promote security of Canada’s telecommunications networks, in consultation with industry.
Mastercard strengthen cyber security consulting practice with new Cyber Front threat simulation platform
In recent years, Mastercard invested in risk quantification, Always-On security monitoring and fraud prevention, to help its customers strengthen their cyber resilience. On 24 May 2022, Mastercard made an announcement of launching a new attack simulation and assessment platform— Cyber Front. The platform will assist businesses and governments enhance their cyber security operational resilience. Cyber Front is enabled by a strategic minority investment in Picus Security.
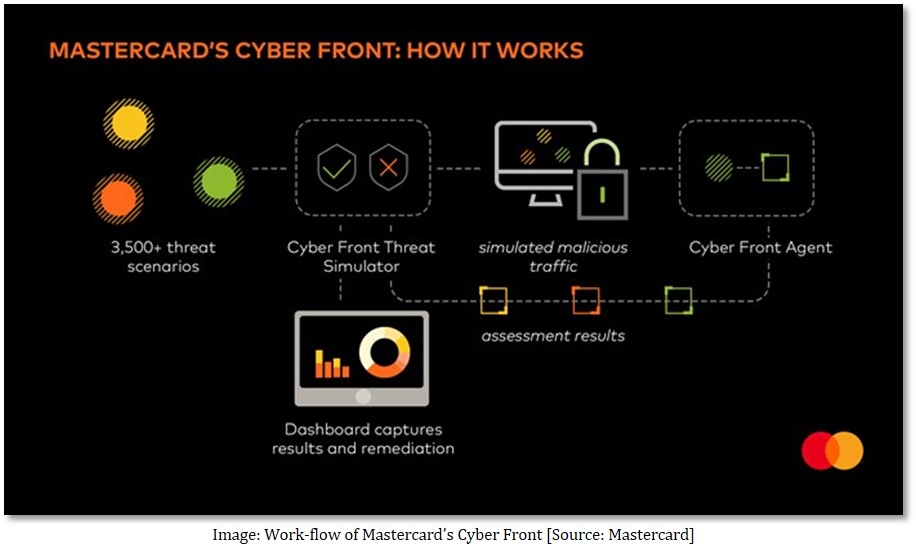
By leveraging a continuously updated library of more than 3,500 real-world threat scenarios, the Cyber Front highlights security gaps and provides mitigation insights in real-time so that organisations can improve upon security investments with continuous validation. The goal of Cyber Front is for organisations to understand if their current systems are effective and identify areas of exposure to ensure greater protection in both— immediate and long term.[7]
Spanish Prime Minister’s phone hacked with Pegasus tool
On 02 May 2022, the Spanish government informed that Prime Minister (PM) Pedro Sanchez’s phone was hacked with Pegasus software. Earlier, in May-June 2021, Spanish Defence Minister— Margarita Robles’ phone was also hacked using the same software. Pegasus software is an Israel-made digital hacking tool to snoop on phone communication.
Researchers investigate and revealed that in April 2022, several political figures in Catalonia were victims of digital espionage. [8] It is assumed that top European Union (EU), the United Kingdom (UK), Poland and Hungary officials may also been targeted with Pegasus software. The use of digital hacking tools such as Pegasus has helped security officials around the world fight crime and ward off national security concerns, therefore, European governments have been wary of delving into the intricacies of spyware programs.[9]
Amid foreign hacking threats, Pentagon contractors looking for software flaws through VDP
Considering Russia and China’s efforts to steal sensitive data from the United States (US) defence industrial base, Pentagon’s pilot program discovered an array of software vulnerabilities with dozens of defence contractors. The objective of pilot program— “Vulnerability Disclosure Program” (VDP) is to identify and fix flaws in the e-mail programs, mobile devices and industrial software used by the Pentagon’s defence contractors before hackers can take advantage of these vulnerabilities.
“We really wanted to focus on those smaller defence contractors that may not have the budget and resources,” said Melissa Vice, interim director of the Department of Defense (DoD) Cyber Crime Centre’s DoD VDP. In the business sector, VDPs are widespread practise, in which vetted cyber professionals scan systems for defects and report them internally. The Pentagon has been running a VDP since 2016, but after the pilot, the intention is to permanently expand the programme to include defence contractors.[10]
Cybercriminals used call forwarding technique to obtain WhatsApp accounts
Cybercriminals used call forwarding as a technique, allowing them to hijack a targeted WhatsApp account and gain control to messages and contact list. The method relied on the mobile carriers’ automated service to forward calls to a different phone number, and WhatsApp’s option to send a OTP (One-Time Password) verification code via voice call.
According to the founder and CEO of ‘CloudSEK’— a digital risk protection company— Rahul Sasi, after knowing the targeted WhatsApp account number and some social engineering, the attacker convinced the victim to make a call to a number that starts with Man Machine Interface (MMI) code that mobile carrier set up to enable call forwarding. A separate MMI code can send all calls to a terminal to a different number or merely when the line is busy or there is no reception, depending on the carrier. “First, you receive a call from the attacker who will convince you to make a call to the following number **67* or *405* (subject to be vary as per the mobile carrier). Within a few minutes, your WhatsApp would be logged out, and the attackers would get complete control of your account”, said Rahul Sasi.
As a protection against such attack, turning on Two-Factor Authentication (TFA) protection in WhatsApp is an effective measure. By requiring a PIN (Personal Identification Number) whenever you register a phone with the messaging app, this feature prevents malicious actors from gaining control of the account.[11]
Endnotes :
[1]India. “CERT-In Advisory CIAD-2022-0014”, Indian Computer Emergency Response Team, 30 May 2022, Available from: https://cert-in.org.in/
[2]“Cisco launches new tool for SMBs to assess their cyber security readiness”, Financial Express, 26 May 2022, Available from: https://www.financialexpress.com/industry/sme/msme-tech-cisco-launches-new-tool-for-smbs-to-assess-their-cybersecurity-readiness/2538348/
[3]India. “7th India-Japan ICT Joint Working Group meeting held under India-Japan ICT Comprehensive Cooperation Framework”, Press Information Bureau- Ministry of Communication, 13 May 2022, Available from: https://pib.gov.in/PressReleasePage.aspx?PRID=1825159
[4]ET Tech. “Government proposes to set up India Data Management Office”, ET Telecom, 28 May 2022, Available from: https://telecom.economictimes.indiatimes.com/news/government-proposes-to-set-up-india-data-management-office/91846155?utm_source=Mailer&utm_medium=ET_batch&utm_campaign=ettelecom_news_2022-05-28&dt=2022-05-28&em=YW51cmFnQHZpZmluZGlhLm9yZw==
[5]India. “Remote Code Execution vulnerability in Apple products”, Indian Computer Emergency Response Team , 20 May 2022, Available from: https://cert-in.org.in/
[6]Canada. “Statement from Minister Champagne on telecommunications security”, Ministry of Innovation, Science and Industry, 19 May 2022, Available from: https://www.canada.ca/en/innovation-science-economic-development/news/2022/05/statement-from-minister-champagne-on-telecommunications-security.html
[7] “Another arrow in the quiver: Mastercard strengthens cybersecurity consulting practice with new cyber front threat simulation platform”, Mastercard, 24 May 2022, Available from: https://www.mastercard.com/news/press/2022/may/another-arrow-in-the-quiver-mastercard-strengthens-cybersecurity-consulting-practice-with-new-cyber-front-threat-simulation-platform/
[8]Aarup, Sarah Anne. “Pegasus spyware targets top Catalan politicians and activists”, Politico, 18 April 2022, Available from: https://www.politico.eu/article/pegasus-spyware-targets-top-catalan-politicians-and-activists/
[9]Manancourt, Vincent. “Hack of Spanish PM’s phone deepens Europe’s spyware crisis”, Politico, 02 May 2022, Available from: https://www.politico.eu/article/pegasus-hacking-spyware-spain-government-prime-minister-pedro-sanchez-margarita-robles-digital-espionage-crisis/
[10]Lyngaas, Sean. “Pentagon contractors go looking for software flaws as foreign hacking threats loom”, CNN, 02 May 2022, Available from: https://edition.cnn.com/2022/05/02/politics/pentagon-defense-contractors-software-flaws/index.html
[11]Ilascu, Ionut. “Hackers steal WhatsApp accounts using call forwarding trick”, Bleeping Computer, 31 May 2022, Available from: https://www.bleepingcomputer.com/news/security/hackers-steal-whatsapp-accounts-using-call-forwarding-trick/

