NATIONAL
MeitY invites applications under the Chips to Start-up (C2S) programme
In line with Prime Minister Modi’s vision of India being next Semiconductor hub, the Ministry of Electronics and Information Technology (MeitY) invited applications from 100 academia, Research & Development (R&D) organisations, Start-ups, and Micro, Small and Medium Enterprises (MSMEs) under its “Chips to Start-up” (C2S) programme. The C2S programme aims to train around 85,000 qualified engineers in the area of Very-Large Scale Integration (VLSI) and Embedded System Design (ESD) over a period of five years. The programme would be implemented at about 100 academic institutions, R&D organisations across India, including IITs, NITs, IIITs, government/private colleges. The Start-ups and MSMEs can also participate in the programme by submitting their proposals under “Academia- Industry Collaborative Project” (AICP). The project proposals should be submitted at C2S portal— www.c2s.gov.in. The institutions applying under the programme should meet the eligibility criteria defined at the portal and should be in line with the proposals’ guidelines. [1]
“No Siri, Alexa, smart devices in close-door meetings”: Intelligence agencies to Govt officials
The intelligence agencies issued a communication security advisory to government officials to control the leaks of classified information. According to news report, the advisory has asked all government officials not to use WhatsApp, Telegram, etcetera, to share confidential information as private tech companies control data storage servers—located outside the country. The advisory also covered instructions on Video Conferencing (VC) and for government officials opted Work from Home (WFH).
“Officials scan classified documents, store them in their mobile, send and share with others through private applications. New devices pose a big risk for national security and must be avoided while discussing important classified or secret issues by all ministries,” said an official on the basis of anonymity. Some of the guidelines in the advisory includes[2]:
i) During meetings where classified issues are to be discussed, officials keep their smartphones and smartwatches outside the meeting room.
ii) In offices—officers and staff shouldn’t keep various office assistant devices like Amazon Echo, Apple HomePod, Google Home, etc.
iii) Digital assistants like Siri and Alexa in smartphones and smartwatches must be switched off while entering a meeting where classified issues will be discussed.
CERT-In issued advisory on “Multiple Vulnerabilities in Apple Products”
On 27 January 2022, the Indian Computer Emergency Response Team (CERT-In) issued an advisory addressing multiple vulnerabilities in Apple products. The vulnerabilities could allow an attacker to gain elevated privileges, execute arbitrary code, disclose sensitive information, and bypass security restriction on the targeted system. The existence of these vulnerabilities based on improper implementation of input validation logic, path validation logic for symlinks, input sanitisation, memory handling and management, state management, bounds checking, restrictions, and checks. A remote attacker could exploit these vulnerabilities by persuading the victim to open a specially crafted file or an application.[3]
India may see rise in Cyber-Espionage in 2022: claimed Kaspersky
According to the Kaspersky’s Cyberthreats to Financial Organisations in 2022 report, India is among top five targets for cyber-attacks in the Asia-Pacific (APAC) region, especially the breaches which involves cyber-espionage. The kind of cyber-attacks that are expected to increase are Advanced Persistent Threats (APTs) attacks with malicious intent to gather significant geopolitical, business, and military intelligence.
“India’s economy and expected growth are among the key reasons for the elevated level of threat it faces. The only correct response is ‘prevention is better than cure’ – to invest in infrastructure and capabilities aimed at improving cyber-intelligence by improving prediction capabilities,” said Dipesh Kaura, General Manager at Kaspersky (South Asia).[4]
BitCoin Fraud: UP Police booked US-based crypto-exchange for fraud
Uttar Pradesh’s Cyber Crime police booked officials of the United States-based crypto-currency exchange firm—Poloniex, for allegedly cheating a Lucknow-based journalist of BitCoins worth ₹ 5.66 lakh. According to the First Information Report (FIR) registered, the victim—Deepak Gidwani bought BitCoins worth ₹ 50,000 in 2018, but never accessed his account due to little knowledge about the digital assets. After login to his BitCoin account on Poloniex’s platform, Deepak tried to withdraw the money which grew almost 10 times and turned out to be ₹ 5.66 lakh. When he tried to withdraw the amount, Deepak was informed that no transaction can be done as the account is frozen. Freezing is a procedure followed by most financial firms if the account is dormant.
“This clearly looks like a case of cheating by the international crypto-exchange firm. On the victim’s complaint, we have booked senior officials of the company along with the CEO. We are now in the process of writing to the company to furnish the account detail of the victim. We will demand logs of his logins and from where the transactions were made,” said Prof Triveni Singh, Superintendent of Police (SP) Cyber Crime, Uttar Pradesh.[5]
CERT-In issued advisory on “multiple vulnerabilities in Microsoft products”
On 12 January 2022, the Indian Computer Emergency Response Team (CERT-In) issued an advisory on multiple vulnerabilities in Microsoft products, including Exchange Servers. These vulnerabilities could be exploited by an attacker to access sensitive information, bypass security restrictions, perform a Denial of Service (DoS) attack, escalating privileges, perform spoofing attacks or executing arbitrary codes on the targeted system.[6]
INTERNATIONAL
Cyber Security researchers uncovered new Iranian hacking campaign targeting Turkish users
In newly published report by Cisco Talos, researchers have discovered malware campaign undertaken by the Iranian “MuddyWater” Advanced Persistent Threat (APT) group targeting Turkey-based private organisations and government establishments, including the Scientific and Technological Research Council of Turkey (TUBITAK). The campaign utilised malicious PDFs, XLS files and Windows executables to deploy malicious PowerShell-based downloaders acting as initial footholds into the target’s enterprise. Earlier of this month, the US Cyber Command linked “MuddyWater” APT to the Iran’s Ministry of Intelligence and Security (MIS).
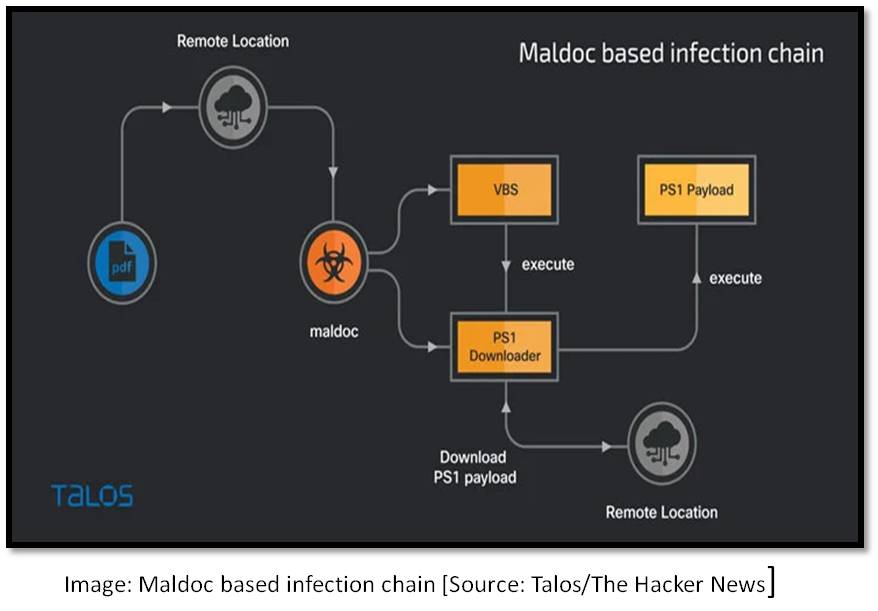
In modus operandi, the malicious documents (maldoc) pretend to be as legitimate documents from the Turkish Health and Interior Ministries, with the attacks starting by executing malicious macros embedded in them to propagate the infection chain and drop PowerShell scripts to the compromised system. The “MuddyWater” used ‘canary tokens’ in the macro code—a mechanism which is being used to track successful infection of targets, thwart analysis, and detect if the payload servers are being blocked at the other end. The canary tokens, also known as honeytokens, are identifiers embedded in objects like documents, web pages and emails, which, when opened, triggers an alert in the form of an HTTP request, alerting the operator that the object was accessed. [7]
Researchers experimented natural silk fibres to generate secure keys for strong authentication
A team of researchers at South Korea’s Gwangju Institute of Science and Technology (GIST) have utilised natural silk fibres from domesticated silkworms to build an environment-friendly digital security system that is believed to be ‘practically unbreachable’. “The first natural Physical Unclonable Function (PUF) takes advantage of the diffraction of light through natural micro-holes in native silk to create a secure and unique digital key for future security solutions,” said researchers.
The Physical Unclonable Functions or PUFs refer to devices that leverage inherent randomness and microscopic differences in electronics introduced during manufacturing to generate a unique identifier, such as cryptographic keys, for a given set of inputs and conditions. In other words, PUFs are non-algorithmic one-way functions derived from uncopiable elements to create unbreakable identifiers for strong authentication. Over the years, PUFs have been widely used in smartcards to provide silicon fingerprints as a means of uniquely identifying cardholders based on a Challenge-Response Authentication (CAR) scheme.[8]
DPRK’s hackers resurfaced with variant of KONNI RAT malware
A cyber-espionage group with strong ties to Democratic People’s Republic of Korea (DPRK), commonly known as North Korea, has re-emerged with a stealthier variant of its Remote Access trojan—KONNI RAT to attack political establishments located in Russian Federation and South Korea. Most recent intrusions are orchestrated by the group involved targeting Russia’s Ministry of Foreign Affairs (MID) with New Year lures to compromise Windows-based systems with malware. The infections, as with other attacks of this kind, starts with a malicious Microsoft Office document that, when opened, initiates a multi-stage process that involves several moving parts that help the attackers elevate privileges, evade detection, and ultimately deploy the KONNI RAT payload on compromised systems.[9]
Endnotes
[1] India. “MeitY invites applications under the Chips to Startup (C2S) Programme from academia, R&D organisations, startups and MSMEs”, Ministry of Electronics and IT, 16 January 2022, Available from: https://pib.gov.in/PressReleasePage.aspx?PRID=1790350. Accessed on 31 January 2022.
[2] “No Siri, Alexa, smart devices in secret meetings: Intel note to Govt officials on tech threats”, Security Today, 27 January 2022, Available from:https://www.securitytoday.in/indian-news/no-siri-alexa-smart-devices-in-secret-meetings-intel-note-to-govt-officials-on-tech-threats/. Accessed on 31 January 2022.
[3]India. “CERT-In advisory CIAD-2022-0005: Multiple Vulnerabilities in Apple products”, Indian Computer Emergency Response Team- Ministry of Electronics and Information Technology, 27 January 2022, Available from: https://cert-in.org.in/
[4] “Kaspersky predicts rise in cyber espionage for India in 2022”, Business Standard, 14 January 2022, Available from: https://www.business-standard.com/article/economy-policy/kaspersky-predicts-rise-in-cyber-espionage-for-india-in-2022-122011401057_1.html . Accessed on 02 February 2022.
[5]Shekhar, Shashank. “Bitcoin Fraud: UP Police books US-based crypto exchange Poloniex for defrauding Lucknow journalist of ₹5.66 lakh”, 31 January 2022, Available from: https://www.the420.in/bitcoin-fraud-up-police-books-us-based-crypto-exchange-poloniex-for-defrauding-lucknow-journalist-of-rs-5-66-lakh/ . Accessed on 02 February 2022.
[6]India. “CERT-In advisory CIAD-2022-0001: Multiple Vulnerabilities in Microsoft products”, Indian Computer Emergency Response Team- Ministry of Electronics and Information Technology, 12 January 2022, Available from: https://cert-in.org.in/
[7]Lakshmanan, Ravie. “Researchers uncover new Iranian hacking campaign targeting Turkish users”, The Hacker News, 31 January 2022, Available from: https://thehackernews.com/2022/01/researchers-uncover-new-iranian-hacking.html . Accessed on 02 February 2022. ; Malhotra, Asheer and Vitor Ventura. “Iranian APT MuddyWater targets Turkish users via malicious PDFs, executables”, CISCO Talos, 31 January 2022. Available from: https://blog.talosintelligence.com/2022/01/iranian-apt-muddywater-targets-turkey.html . Accessed on 02 February 2022.
[8] “Gwangju Institute of Science and Technology Researchers Develop Novel Silk-based Digital Security Device”, Gwangju Institute of Science and Technology (GIST), 24 January 2022, Available from: https://www.gist.ac.kr/_prog/bbs/?mode=V&site_dvs_cd=en&menu_dvs_cd=060208&code=060208&no=203961 . Accessed on 02 February 2022.
[9]Lakshmanan, Ravie. “North Korean hackers return with stealthier variant of KONNI RAT malware”, The Hacker News, 28 January 2022, Available from: https://thehackernews.com/2022/01/north-korean-hackers-return-with.html. Accessed on 03 February 2022.

