The Facebook’s subsidiary company—WhatsApp, on 29 October 2019, filed a lawsuit in the United States California’s Northern District Federal Court against Israel-based cyber-arms1 firm— the NSO Group, for infecting ‘specific’ group of WhatsApp users worldwide, mainly belong to civil societies, through their spyware2 program—Pegasus (also known as Trident). In the lawsuit, filed under the US Computer Fraud and Abuse Act, WhatsApp claimed that NSO Group developed the program and targeted 1400 devices with its malware. As claimed by WhatsApp, between 29 April – 10 May 2019, the surveillance was carried out on users based in 20 countries and the NSO Group illegally obtained the information from the users’ cellular/mobile devices without their consent.3 In India, WhatsApp has more than 400 million (or 40 crore) active users,4 out of its global reach of 1.5 billion users. The statistics supports the fact that India remains WhatsApp’s biggest market among other nations. Facebook confirmed that among other targeted 1400 users worldwide, Pegasus also targeted at least two dozen Indian journalists, activists, academicians, and lawyers.5 In its lawsuit, WhatsApp did not name the entity or a State who used this spyware program but accused the NSO group— an organisation that designed the Pegasus program.
The NSO Group and Pegasus
Founded in 2009, the NSO Group (NSO is an abbreviation of the names of firm’s founders— Niv Carmi, Shalev Hulio, and Omri Lavie) is an Israel-based company renowned for its Pegasus spyware to undertake remote surveillance of the smartphones.6 On its official website, the company states that the “NSO group licenses its products only to government intelligence and law enforcement agencies for the sole purpose of preventing and investigation of terrorism and serious crime”.7 However, few reports claimed that the Pegasus, created by the NSO group, was used for surveillance on Human Rights activists, and journalists, and in early 2019 it was used for State-on-State espionage in Pakistan. According to anonymous sources, at least two dozen of Pakistan’s senior defence and intelligence officials were allegedly targeted. This underscore the fact that Pegasus can be utilised for State-to-State espionage.8 It was also revealed that in 2017, the NSO group offered Saudi Arabia a system which does surveillance of the cellphones— believed to be Pegasus. The offer was made to the Saudi Arabia Crown Prince Mohammed Bin Salman who began the purging of regime opponents.9 Some reports linked the sale of the spyware with the killing of Saudi Arabia dissident journalist—Jamaal Khashoggi. In an interview with CBS on 24 March 2019, the NSO Group’s CEO Shalev Hulio was asked on the sale of the Pegasus phone surveillance program to the Saudis for USD 55 million. In his reply, Hulio said that he would not talk about a specific customer.10
Pegasus- an arsenal of technical powers
In 2016, Pegasus program was discovered by the Citizen Lab—an interdisciplinary laboratory based at the University of Toronto, Canada. In an act of social engineering, the UAE (United Arab Emirates)-based Human Rights activist— Ahmed Mansoor received a text message with a link on his iPhone which promised the disclosure of “secrets” regarding the tortures in UAE prisons. Suspecting something unusual, Mansoor sent the message (along with link) to the Citizen Lab for further investigation. The investigation jointly carried out by the Citizen Lab and the Lookout (a private IT Security company based in California, US) revealed one of the most sophisticated cyber-weapons ever deployed—a spyware with the capability of performing surveillance and collection of “text messages, photos, emails, location data, device’s microphone and camera”.11 Had Mansoor clicked on the link provided in the message, it would have resulted in a ‘jailbreak’ on his cellular phone by installing the Pegasus program.
In 2018, The Times of Israel reported that the government of UAE has used the Pegasus program since 2003. 12 On 31 August 2018, The New York Times reported that the UAE government used the Pegasus program for more than a year, targeting the smartphones of dissidents within the country or rivals based abroad for surveillance purposes.13 Not only the UAE, but the Mexican government has also used Pegasus for surveillance on the journalists, activists and their families, who are government’s critics. In 2011, three of Mexico’s Federal agencies have purchased the Pegasus program on the cost of USD 80 million from the NSO group. 14
The phenomenon of ‘Pegasus’ origin is from the Greek mythology where an immortal, winged horse with an ability to fly, had an arsenal of supernatural powers—a free passage from the mortal to the immortal realm. Equipped with powerful coding, the NSO group’s Pegasus program can survive OS (Operating System) reboot, factory resets, and OS upgrades. 15 Other than Android and iOS, it can breach into the Symbian and Blackberry OS devices. It can infiltrate the smartphones, irrespective of the OS, in incognito mode and majorly work on three aspects:- 16
- collection of the historical data on the device,
- continuous monitoring of the activities or actions, and
- transmission of the data to third-party anonymously.
Post-infiltration of a smartphone or cellular device, the Pegasus scans the device and prevents the device from downloading any updates which would identify the malicious program and get rid of it by updating the OS security. Further, the Pegasus installs some essential modules (set of instructions which separate the functionality of a program to work independently to attain the aspect of program) to read the messages, mail, listen to calls (both incoming and outgoing—including Internet calls), capture screenshots as per program instructions, log the keys pressed, capture browser history, contact lists, and monitor every event which has occurred in the device.17 Interestingly, packed with powerful and sophisticated keylogging program and audio recording programs, Pegasus is capable of defying the WhatsApp’s ‘End-to-End Encryption’ feature by “stealing messages before the encryption, and post-decryption in case of incoming messages”.18 At the end of its surveillance operation, the Pegasus program is equipped with self-destruct instructions under which it removes itself from the device(s) to ensure that it cannot be traced back. “Within the payload of the program, there is the ability to erase itself from the device remotely, so when they want to terminate spying (surveillance) on a device, they can remotely destruct it without access to the device itself”, explained Andrew Blaich— Manager of Vulnerability Research at The Lookout. 19
Pegasus’ Case of Indian Users
In early May 2019, WhatsApp discovered a vulnerability in the audio call feature of the application which allows the caller or an attacker to install the spyware or malicious program on the targeted device irrespective of the call answered or unanswered. WhatsApp’s parent organisation Facebook issued an advisory ‘CVE-2019-3568’ with a patch to fix “a buffer overflow vulnerability in WhatsApp VOIP stack allowed remote code execution”.20 On 20 May 2019, WhatsApp submitted an incident report to the Indian Computer Emergency Response Team (CERT-In) stating that it has “identified and fixed a vulnerability which could have enabled an attacker to insert and execute a code on cellular devices”. 21 Raising the issue on behalf of WhatsApp users in India, the government of India expressed its concern over the digital privacy infringement of Indian citizens. The Government of India (GoI) had sought an explanation from the WhatsApp on the nature of the breach and the safety measure that need to be implemented to safeguard the privacy of millions of Indian citizens and expected a reply by 04 November 2019, said Minister the Electronics and Information Technology (MoEIT) Ravi Shankar Prasad.22 On 02 November 2019, WhatsApp replied to the Ministry of Electronics and Information Technology (MoEIT) with the confirmation of exploitation of their platform by a spyware program—Pegasus, developed by the NSO Group. On 26 November 2019, CERT-In had sent a notice to the NSO Group and sought details about the Pegasus and the impact on Indian users.23
According to a report by the Citizen Lab, the Pegasus targeted and infected WhatsApp users based in of 45 countries, including India, Brazil, Canada, France, Israel, Pakistan, Singapore, South Africa, and Switzerland. For its operation in South Asia, the operator was code-named “Ganges” (named after a Holy river in India) targeting India, Bangladesh, and Pakistan since June 2017. The Pegasus program, believed to be, had targeted eight telecoms in India, including Bharti Airtel, MTNL, and Hathaway. 24 In November 2019, following the lawsuit against the NSO Group, WhatsApp confirmed that around 20 people were contacted and alerted about a suspicion that their devices had been targeted for surveillance for two-weeks until May 2019.
What is Ahead for India?
Various media reports on WhatsApp snooping scandal has managed to raise concerns on digital privacy and protection. In context to India, the Ministry of Electronics and Information Technology (MoEIT) replied to a question regarding GoI’s alleged involvement in the WhatsApp surveillance over its citizen through the Pegasus program. The MoEIT confirmed that no Indian government entity was involved in the data infringement of any Indian citizen. 26 Despite the absence of data protection bill, the IT (Information Technology) Act of India is equipped with suitable provisions. The Ministry of Electronics and Information Technology is working on the Personal Data Protection Bill (PDPB) to protect the privacy of its netizens. As mentioned earlier in this article, in case of Pakistan, the Pegasus program was used as a part of State-on-State espionage, a situation cannot be ignored in which Pakistan may use or might be already using Pegasus program against India—targeting senior defence officials and politicians.
In India, the surveillance programs have been used for issue related to terrorism and national security. Most of the surveillance programs were initiated post-2008 Mumbai terror attacks. In 2013, GoI established NATGRID (National Intelligence Grid) which provides data to 11 intelligence and law-enforcement agencies real-time access to 21 sources of citizens’ data to track terror and anti-India activities. The information from these sources include bank account details, telephone records, Passport-related data, and Vehicle Registration details.27 On the other side, as a part of a counter-terrorism strategy, India may deploy the Pegasus program to do the eavesdropping on the communication channels of the terrorist groups. In November 2019, India had planned to push a mandate on data localisation concept which will compel the digital companies to store data of Indian users within the geographical boundaries of India. If the data localisation would have been there, the investigation of the data infringement cases using the spyware program such as Pegasus would have been easier, effective, and timely.
End notes
- Cyber-Arms referred to markets and associated events for the sale of zero-day exploits, cyberweaponry, and other tools. It could be used for both grey and black markets- offline and online.
- Spyware: a software that aims to gather user’s information without his or her consent and transmit the information to another identity or its source.
- TNN. “Govt ask WhatsApp to explain breach amid phone snoop row”, The Times of India, 01 November 2019, Available from: https://timesofindia.indiatimes.com/business/india-business/govt-asks-whatsapp-to-explain-breach-amid-phone-snoop-row/articleshow/71844315.cms
- Manish Singh. “WhatsApp reaches 400 million users in India, its biggest market”, Tech Crunch, 26 July 2019, Available from: https://techcrunch.com/2019/07/26/whatsapp-india-users-400-million/
- Shruti Dhapola. “Explained: What is Israeli spyware Pegasus, which carried out surveillance via WhatsApp?”, The Indian Express, 02 November 2019, Available from: https://indianexpress.com/article/explained/whatsapp-spyware-pegasus-india-surveillance-nso-israel-6096910/
- Orr Hirschauge and Inbal Orpaz. “U.S. Fund to Buy NSO and its Smartphone-snooping software”, Haaretz, 17 February 2014, Available from: https://www.haaretz.com/israel-news/business/u-s-fund-to-buy-snooping-software-1.5323394
- “Governance”, The NSO Group, Available from: https://www.nsogroup.com/governance/
- Stephanie Kirchgaessner. “Israeli spyware allegedly used to target Pakistani officials’ phone”, The Guardian, 19 December 2019, Available from: https://www.theguardian.com/world/2019/dec/19/israeli-spyware-allegedly-used-to-target-pakistani-officials-phones
- Amos Harel, Chaim Levinson, and Yaniv Kubovich. “Israeli Cyber Firm Negotiated Advanced Attack Capabilities Sale With Saudis, Haaretz Reveals”, Haaretz, 25 November 2018, Available from: https://www.haaretz.com/israel-news/.premium-israeli-company-negotiated-to-sell-advanced-cybertech-to-the-saudis-1.6680618
- Rebecca Falconer. “Israeli firm won’t say if it sold spyware linked to Khashoggi killing”, Axios, 25 March 2019, Available from: https://www.axios.com/hacking-firm-nso-saudi-sale-no-comment-khashoggi-b0d4f4d1-9218-4614-b1f1-03495f8be67f.html
- Dave Lee. “Who are the hackers who cracked the iPhone?”, BBC News, 26 August 2016, Available from: https://www.bbc.com/news/technology-37192670
- TOI Staff. “Lawsuits claim Israeli spyware firm helped UAE regime hack opponents’ phones”, The Times of Israel, 31 August 2018, Available from: https://www.timesofisrael.com/lawsuits-claim-israeli-spyware-firm-helped-uae-hack-opponents-phones/
- David D. Kirkpatrick and Azam Ahmed. “Hacking a Prince, an Emir and a Journalist to Impress a Client”, The New York Times, 31 August 2018, Available from: https://www.nytimes.com/2018/08/31/world/middleeast/hacking-united-arab-emirates-nso-group.html
- Azam Ahmed and Nicole Perlroth. “Using texts as lures, government spyware targets Mexican journalists and their families”, The New York Times, 19 June 2017, Available from: https://www.nytimes.com/2017/06/19/world/americas/mexico-spyware-anticrime.html
- Dinesh Narayanan and Venkat Ananth. “Pegasus spyware can target up to 50 phones at once”, The Economic Times, 02 November 2019, Available from: https://economictimes.indiatimes.com/tech/internet/pegasus-spyware-can-target-up-to-50-phones-at-once/articleshow/71860858.cms?from=mdr
- Prasid Banerjee. “What is Pegasus, the chosen tool for ‘total surveillance’?”, Live Mint, 01 November 2019, Available from: https://www.livemint.com/technology/tech-news/what-is-pegasus-the-chosen-tool-for-total-surveillance-11572578636720.html
- John Snow. “Pegasus: The ultimate spyware for iOS and Android”, Kaspersky daily, 11 April 2017, Available from: https://www.kaspersky.com/blog/pegasus-spyware/14604/
- Ibid.
- Danny Palmer. “Trident iOS flaws: Researchers detail how the spyware stayed hidden”, ZDNet, 07 November 2016, Available from: https://www.zdnet.com/article/trident-ios-flaws-researchers-detail-how-the-spyware-stayed-hidden/
- “CVE-2019-3568”, Facebook, Available from: https://www.facebook.com/security/advisories/cve-2019-3568
- Government of India. “Withdrawal of WhatsApp security vulnerability warning from the CERT-In website”, Ministry of Electronics and Information Technology, Unstarred question no-2747, Rajya Sabha, 12 December 2019, Available from: http://pqars.nic.in/annex/250/Au2747.pdf
- TNN. “Govt ask WhatsApp to explain breach amid phone snoop row”, The Times of India, 01 November 2019, Available from: https://timesofindia.indiatimes.com/business/india-business/govt-asks-whatsapp-to-explain-breach-amid-phone-snoop-row/articleshow/71844315.cms
- “Unstarred Question No- 1951”, Rajya Sabha- Ministry of Electronics and Information Technology, 05 December 2019, Available from: http://pqars.nic.in/annex/250/Au1951.pdf
- FP Staff. “Pegasus spyware infected 45 countries between 2016 and 2018, targeted eight Indian telcos, shows citizen lab report”, First Post, 01 November 2019, Available from: https://www.firstpost.com/world/pegasus-spyware-infected-45-countries-between-2016-and-2018-targeted-eight-indian-telcos-shows-citizen-lab-report-7583381.html
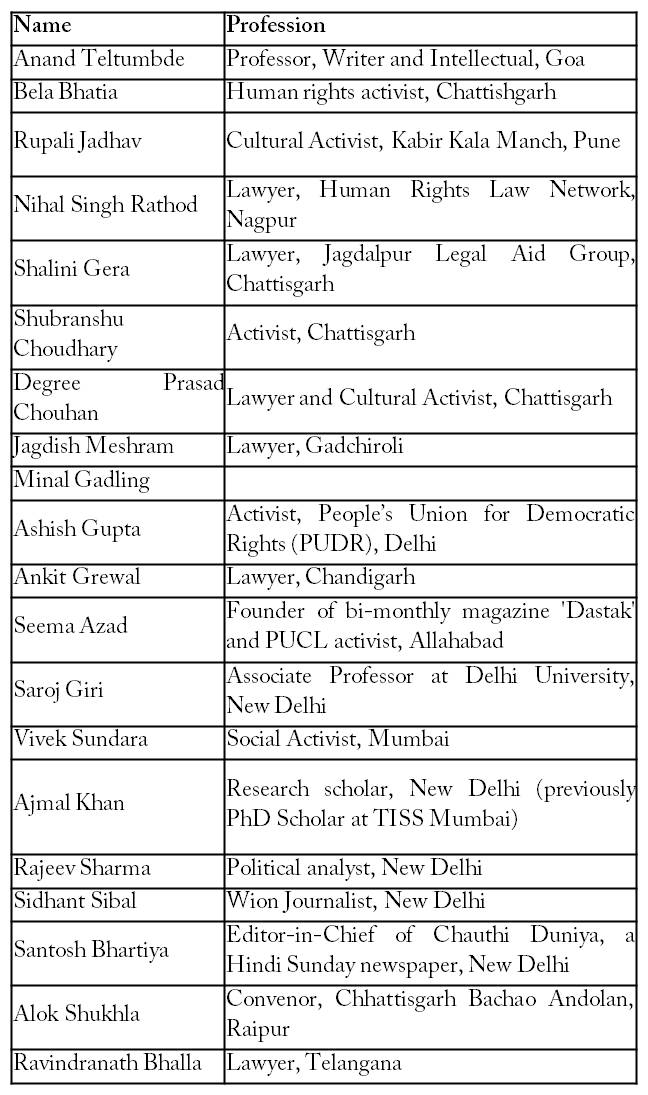
- “Table 1. List of people whose devices were possibly infected by the Pegasus program”, First Post, Available from: https://www.firstpost.com/india/israeli-pegasus-snooping-case-the-full-list-of-activists-who-have-confirmed-being-contacted-by-whatsapp-over-surveillance-concerns-7582151.html
- Government of India. “Data Breach in WhatsApp”, Unstarred Question No. 1155, Ministry of Electronics and Information Technology, Rajya Sabha, 28 November 2019, Available from: https://pqars.nic.in/annex/250/AU1155.pdf
- Maria Xynou. “Big democracy, big surveillance: India’s surveillance state”, OpenDemocracy, 10 February 2014, Available from: https://www.opendemocracy.net/en/opensecurity/big-democracy-big-surveillance-indias-surveillance-state/
(The paper is the author’s individual scholastic articulation. The author certifies that the article/paper is original in content, unpublished and it has not been submitted for publication/web upload elsewhere, and that the facts and figures quoted are duly referenced, as needed, and are believed to be correct). (The paper does not necessarily represent the organisational stance... More >>
Image Source:https://media.kasperskydaily.com/wp-content/uploads/sites/92/2017/04/06020657/pegasus-mobile-spyware-featured-1.jpg











Post new comment