

The Central government supplements the initiatives of the State Governments through various advisories and schemes for the capacity building of their law-enforcement agencies (LEAs). Along with, the Central Government has taken steps to strengthen the mechanism to deal with cyber-crimes in a comprehensive and coordinated manner. Following steps has taken in the regards[1]:
i) The Ministry of Home Affairs (MHA) has set up the ‘Indian Cyber Crime Coordination Centre (I4C) to deal with all types of cyber-crime in India, in coordinated and comprehensive manner.
ii) The National Cyber Forensic Laboratory (NCFL) has been established at CyPAD, Dwarka, New Delhi, to provide early phase cyber forensic assistance to Investigating Officers (IOs) of State/Union Territory Police.
iii) ‘CyTrain’ portal—Massive Open Online Courses (MOOC) platform, has been deployed under the I4C, for capacity building of Police officers, Judicial officers through online courses on critical aspects of cyber-crime investigation, forensics, prosecution, etcetera, along with certification.
iv) The National Cyber Crime reporting portal— www.cybercrime.gov.in [2] has been launched as a part of I4C, to enable public to report incidents pertaining to all types of cyber-crimes.
v) Citizen Financial Cyber Fraud (CF2) reporting and management system, under I4C, has been launched for immediate reporting of financial frauds and to stop siphoning off funds by the fraudsters.
vi) Seven ‘Joint Cyber Coordination Teams (JCCT)’ have been constituted under I4C, covering the entire nation based upon cyber-crime hotspots/areas having multi-jurisdictional issues.
On 24 February 2022, the Ministry of Electronics and Information Technology (MeitY) released a “National Strategy on Additive Manufacturing”, to cater next-generation digital manufacturing and mitigate immediate disabilities of local industries. On the occasion, the Union Minister of Electronics & Information Technology, Communications & Railways—Ashwini Vaishnaw stated that through the strategy, India is focusing on 50 ‘India-specific’ technologies, 100 new start-ups, 500 products, 10 existing and new manufacturing sectors, and one lakh new skilled human resource. “Manufacturing sector is an important part of Prime Minister’s vision for USD 1 trillion Digital Economy. Additive manufacturing is next-generation of digital manufacturing which allows the intersection of computer electronics, imaging, and the emerging areas of Artificial Intelligence (AI), Pattern Recognition, and will help in creating Intellectual Property (IP) & Export opportunities,” emphasised Rajeev Chandrasekhar, Minister of State for Electronics & Information Technology and Skilled Development & Entrepreneurship.
With the release of strategy, innovation and Research & Development (R&D) ecosystem will be encouraged in PPP mode to transform existing research knowledgebase to develop Additive Manufacturing grade materials, 3D printer machines and printed indigenous products for vast domestic and international market in various sectors including electronics, photonics, medical device, agriculture, and food processing. The national strategy would postulate the tenets of ‘Make in India’ and ‘Atmanirbhar Bharat Abhiyan’ that advocate self-reliance through technological transformation of the production paradigm.[2]
On 09 February 2022, the Indian Computer Emergency Response Team (CERT-In) issued an advisory— CIAD-2022-0006, regarding multiple vulnerabilities found in various Microsoft products, including Windows Operating System, SharePoint, Developer Tools.[3]The vulnerabilities could be exploited by an attacker to escalate privilege, execute arbitrary code, disclose sensitive information, bypass security restrictions, spoofing attacks, and perform Denial of Service (DoS) attack on the targeted system. The advisory also suggested companies and individuals to apply appropriate security updates offered by the vendor—Microsoft.
On 22 February 2022, the Indian Computer Emergency Response Team (CERT-In) issued an alert on spread of ‘LockBit 2.0 Ransomware’ malware. The LockBit 2.0 operates as an affiliate-based Ransomware-as-a-Service (RaaS) ramped up its targeted attacks. According to the alert, the LockBit 2.0 spreads through various techniques, including, purchased access, unpatched vulnerabilities, insider access, and Zero-day exploits.
It is also reported that LockBit threat actors are actively exploiting existing vulnerabilities in the Fortinet FortiOS and FortiProxy products, identified as CVE-2018-13379, in order to gain initial access to specific victim networks. After compromising a victim network, LockBit 2.0 actors use publicly available tools such as Mimikatz to escalate privileges. LockBit 2.0 also abuses legitimate tools such as Process Hacker and PC Hunter to terminate processes and services in the victim system. [4]
On 26 February 2022, the Union Cabinet, chaired by Indian Prime Minister (PM) Narendra Modi, has approved the Central Sector Scheme (CSS)— Ayushman Bharat Digital Mission (ABDM) of Ministry of Health and Family Welfare, Government of India, with budget of ₹ 1,600 crore for five years. The National Health Authority (NHA) will be the implementing agency of ABDM. Over the years, digital health solutions across healthcare ecosystem have proven to be beneficial, with CoWIN, AarogyaSetu, and e-Sanjeevani, further demonstrating the role technology can play in enabling access to healthcare.
Based on foundations from various digital initiative, such as Jan Dhan, Aadhaar and Mobile (JAM) trinity and other digital initiatives of the government, ABDM will be creating a seamless online portal through the provisions of a wide-range of data, information and infrastructure services, duly leveraging open, interoperable, standards-based digital systems while ensuring the security, confidentiality and privacy of health-related personal information. The pilot project of ABDM was completed in the six Union Territories (UTs)—Ladakh, Chandigarh, Dadra & Nagar Haveli, Daman & Diu, Puducherry, Andaman & Nicobar Islands, and Lakshadweep with successful demonstration of technology platform developed by the NHA. During the pilot, digital sandbox was created in which more than 774 partner solutions are undergoing integration. As on 24th February 2022, 17,33,69,087 Ayushman Bharat Health Accounts have been created and 10,114 doctors and 17,319 health facilities have been registered in ABDM. [5]
On 28 February 2022, Telecom Sector Skill Council (TSSC) and Delhi Skill and Entrepreneurship University (DSEU) signed a Memorandum of Understanding (MoU) to deliver skills and relevant courses in technologies such as 5G, Artificial Intelligence (AI), Machine Learning (ML), and Internet of Things (IoTs), to DSEU students and other aspirants in Delhi/NCR region. “The partnership has a lot of potential to create a stir in the skill ecosystem and potentially lead to a long duration degree (usually of three years) course on telecom which will be wholeheartedly welcomed by the industry,” said Arvind Bali, CEO, TSSC. [6]
A statement released by Internet and Mobile Association of India (IAMAI), on 24 February 2022, suggested that the Joint Committee of the Parliament (JCP)’s report on the Personal Data Protection (PDP) Bill 2019, is out of synchronisation with India’s ambitions for the current decade in the field of technology. In December 2021, the JCP report was submitted with recommendations, including stringent data localisation norms, expanded scope to non-personal data, new frameworks for Software and hardware testing.
In a recent interview to a publication, Minister of Communications, Railways, and Electronics & Information Technology— Ashwini Vaishnaw acknowledged on the subject and informed that there are few issues which are tricky and need resolution. The Parliamentary Committee has made some suggestions. [7]
On 23 February 2022, Minister of State (MoS) for Electronics & Information Technology— Rajeev Chandrasekhar said that the government of India is bringing a resolution that will make organisations hit by cyber-attack to report or disclose it before the government. While speaking at the launch of the IBM Security Command Centre for Asia Pacific region established in Bangaluru, MoS Chandrasekhar informed that about 100 million-odd cyber incidents have been reported by Indian Computer Emergency Response Team (CERT-In) so far, and India is reportedly second-most attacked country as far as cyber-crime is concerned. “It is essential that at any given point, government and its agencies have absolute clarity on the threat matrix that is around and is active in cyberspace in India,” said MoS Chandrasekhar. [8]
Researchers at the Microsoft Threat Intelligence Centre (MSTIC) observed destructive cyber-attacks targeting Ukrainian digital infrastructure and spotted a malware strain—FoxBlade, several hours before Russia’s military operations over Ukraine on 24February 2022. On 23 February 2022, Symantec and ESET spotted the malware. “We immediately advised the Ukrainian government about the situation, including our identification of the use of new malware package (FoxBlade), and provided technical advice on steps to prevent the malware’s success,” said Microsoft President and Vice-Chair Brad Smith.[9]
Earlier in 2017, NotPetya malware attack had impacted Ukraine’s and other countries’ economies. The NotPetya attack was linked to Russia’s GRU Main Intelligence Directorate hacking group—Sandworm.
According to the technical report released by Symantec’s Threat Hunter team, on 28 February 2022, Daxin— a China linked stealthy backdoor specifically designed for deployment in hardened corporate networks that feature advanced threat detection capabilities. Daxin is the most advanced backdoor program ever deployed by China-linked cyber actors. “Considering its capabilities and the nature of its deployed attacks, Daxin appears to be optimised for use against stealth networks, allowing attackers to burrow deep into target’s network and exfiltrate data without raising any suspicions,” read Symantec’s report.
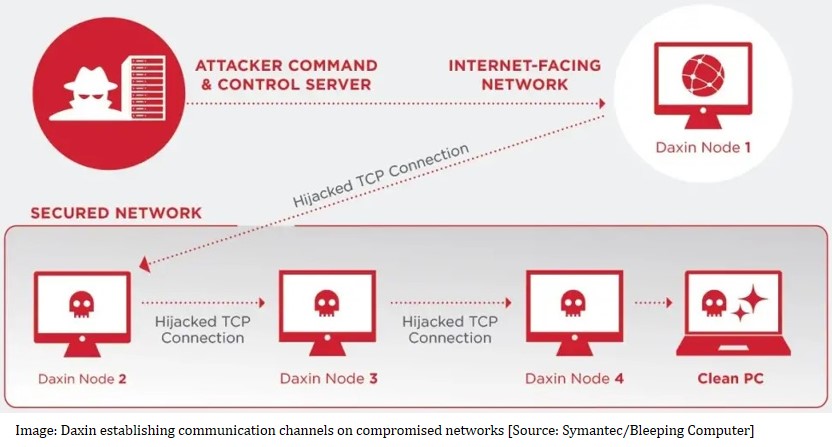
By hijacking TCP connections, the Daxin malware can hide malicious communication in what is perceived as legitimate traffic and thus remain undetected. Daxin also stands out due to its capability to establish intricate communication pathways across multiple infected computers at once, using a single command to a set of nodes. This allows threat actors to re-establish the connections and encrypted communication channels in well-guarded networks.[10]
The United States (US) on 24 February 2022, restricted exports to Russia of a broad set of US-made products as well as foreign-produced goods built with US technology, following Russia’s military operation in Ukraine. The new rules will force companies making tech products overseas with US tools to seek a US license before shipping to Russia. The Semiconductor Industry Association (SIA), which represents US chipmakers, noted that “Russia is not a significant direct consumer of semiconductors; and Russia’s communications and tech spending was only about USD 25 million out of the multi-trillion global market in 2019.” [11]
On 22 February 2022, a coalition of 31 groups and academics under the pan-European consumer group—BEUC, said that individual users should be allowed to sue United States (US)-base tech giants for breaching critical European Union (EU) rules. The draft Digital Market Acts (DMA) sets out a lot of ‘do’s’ and ‘don’ts’ for online watchdogs, in effect targeting Apple, Google, Facebook parent Meta, Amazon, and Microsoft. The DMA allows business users to sue violating companies. “The DMA must enable users, both individually and collectively, to bring enforcement actions for violation of DMA rules before national courts,” read the open letter to EU institutions.[12]
[1]Government of India. “Advance Centre for Cyber Security”, Press Information Bureau, 08 February 2022, Available from: https://www.pib.gov.in/PressReleasePage.aspx?PRID=1796568 [3]
[2]Government of India. “Shri Ashwini Vaishnaw, Minister of Electronics and IT and Shri Rajeev Chandrasekhar, Minister of State in Electronics and IT release ‘National Strategy on Additive Manufacturing’”, Press Information Bureau, 24 February 2022, Available from: https://www.pib.gov.in/PressReleasePage.aspx?PRID=1800915 [4]
[3]CERT-In. “CERT-In Advisory CIAD-2022-0006: Multiple Vulnerabilities in Microsoft Product”, CERT-In, 09 February 2022, Available from: https://www.cert-in.org.in/ [5]
[4]CERT-In. “LockBit 2.0 Ransomware”, Cyber Swachhta Kendra, 22 February 2022, Available from: https://www.csk.gov.in/alerts/LockBit_2.0_Ransomware.html [6]
[5]Cabinet Committee on Economic Affairs. “Cabinet approves implementation of Ayushman Bharat Digital Mission with a budget of Rs.1,600 crore for five years”, Press Information Bureau, 26 February 2022, Available from: https://pib.gov.in/PressReleasePage.aspx?PRID=1801322 [7]
[6]ET Telecom. “TSSC, DSEU sign MoU to impart skills in 5G, AI/ML, IoT technologies”, ET Telecom, 28 February 2022, Available from: https://telecom.economictimes.indiatimes.com/news/tssc-dseu-sign-mou-to-impart-skills-in-5g-ai/ml-iot-technologies/89891798 [8]
[7]Majumdar, Romita. “JCP recommendations on PDP Bill will negatively impact India’s tech ambitions: IAMAI”, 24 February 2022, Available from: https://telecom.economictimes.indiatimes.com/news/jcp-recommendations-on-pdp-bill-will-negatively-impact-indias-tech-ambitions-iamai/89808830 [9]
[8]PTI. “Regulation coming to put onus of cyber-crime reporting on organisations: MoS IT”, ET Telecom, 23 February 2022, Available from: https://telecom.economictimes.indiatimes.com/news/regulation-coming-to-put-onus-of-cyber-crime-reporting-on-organisations-mos-it/89774913 [10]
[9]Smith, Brad. “Digital technology and the war in Ukraine”, Microsoft, 28 February 2022, Available from: https://blogs.microsoft.com/on-the-issues/2022/02/28/ukraine-russia-digital-war-cyberattacks/ [11]
[10]Toulas, Bill. “Chinese cyberspies target govts with their ‘most advanced’ backdoor”, Bleeping Computer, 28 February 2022, Available from: https://www.bleepingcomputer.com/news/security/chinese-cyberspies-target-govts-with-their-most-advanced-backdoor/ [12] ; Threat Hunter Team. “Daxin: Stealthy backdoor designed for attacks against hardened networks”, Symantec Blog, 28 February 2022, Available from: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/daxin-backdoor-espionage [13]
[11]Reuters. “The new US export rules designed to freeze Russian tech”, ET Telecom, 25 February 2022, Available from: https://telecom.economictimes.indiatimes.com/news/the-new-u-s-export-rules-designed-to-freeze-russian-tech/89815175 [14]
[12]Reuters. “Users should be allowed to sue US tech giants under EU rules, civil groups say”, ET Telecom, 22 February 2022, Available from: https://telecom.economictimes.indiatimes.com/news/users-should-be-allowed-to-sue-u-s-tech-giants-under-eu-rules-civil-groups-say/89741797 [15]
Links:
[1] https://www.vifindia.org/2022/march/13/vif-cyber-review
[2] http://www.cybercrime.gov.in
[3] https://www.pib.gov.in/PressReleasePage.aspx?PRID=1796568
[4] https://www.pib.gov.in/PressReleasePage.aspx?PRID=1800915
[5] https://www.cert-in.org.in/
[6] https://www.csk.gov.in/alerts/LockBit_2.0_Ransomware.html
[7] https://pib.gov.in/PressReleasePage.aspx?PRID=1801322
[8] https://telecom.economictimes.indiatimes.com/news/tssc-dseu-sign-mou-to-impart-skills-in-5g-ai/ml-iot-technologies/89891798
[9] https://telecom.economictimes.indiatimes.com/news/jcp-recommendations-on-pdp-bill-will-negatively-impact-indias-tech-ambitions-iamai/89808830
[10] https://telecom.economictimes.indiatimes.com/news/regulation-coming-to-put-onus-of-cyber-crime-reporting-on-organisations-mos-it/89774913
[11] https://blogs.microsoft.com/on-the-issues/2022/02/28/ukraine-russia-digital-war-cyberattacks/
[12] https://www.bleepingcomputer.com/news/security/chinese-cyberspies-target-govts-with-their-most-advanced-backdoor/
[13] https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/daxin-backdoor-espionage
[14] https://telecom.economictimes.indiatimes.com/news/the-new-u-s-export-rules-designed-to-freeze-russian-tech/89815175
[15] https://telecom.economictimes.indiatimes.com/news/users-should-be-allowed-to-sue-u-s-tech-giants-under-eu-rules-civil-groups-say/89741797
[16] http://www.facebook.com/sharer.php?title= VIF Cyber Review: February 2022&desc=&images=&u=https://www.vifindia.org/2022/march/13/vif-cyber-review
[17] http://twitter.com/share?text= VIF Cyber Review: February 2022&url=https://www.vifindia.org/2022/march/13/vif-cyber-review&via=Azure Power
[18] whatsapp://send?text=https://www.vifindia.org/2022/march/13/vif-cyber-review
[19] https://www.vifindia.org/author/anurag-sharma